
解读综述
2019年9月NIST发布Draft NIST Special Publication 800-207后,开始广泛征求修改意见,并于2020年2月发布最新版本Draft(2nd) NIST Special Publication 800-207。Draft2发布后,奇安信战略咨询规划已经第一时间将两版标准草案进行了对比总结与评述,可参见“《零信任架构》NIST标准草案第2版正式发布和主要变化”。
在本文中,奇安信身份安全实验室将对两版标准进行详细的对比。与Draft1相比,NIST在Draft2中做了大量细致的修改及修正工作,并在原有基础上进行内容扩充新增部分章节。由此可见NIST对《零信任架构》标准的重视,正在加快标准推进的步伐。值得注意的是,Draft2中对零信任历史的追溯到了国防信息系统局(DISA)和国防部(DOD)公布的“BlackCore”(黑核)项目,将零信任标准与美国国防部建立了关联,可以推断出美国国防部也参与并影响了标准草案工作,一定意义上也是零信任标准加速的有力推手。
在详细对比Draft2与Draft1后,可以看出NIST认为更多的组织/机构能够受益于零信任架构。通过提供多种零信任实现方式,NIST希望ZTA不仅能在大型企业落地,同时在小型企业中也能发挥作用。不管采用何种方式(增强的身份治理驱动、微分段、以及基于网络基础架构和SDP等)实现,ZTA应该围绕着企业本身的资产防护且遵守零信任原则宗旨进行,而具体的实现方式应充分结合企业现状。同时,风险评估也成为零信任的重要内容之一,企业如果希望向ZTA迁移,在考虑技术替代的同时,也要重视风险评估工作。
NIST在Draft2中再次强调【零信任是一种以资源保护为核心的网络安全范式,其前提是信任从来不是隐式授予的,而是必须进行持续评估。】Draft2对Draft1的一些主要变化可以分为新增、修改两部分。
第一部分、新增部分
Draft2中新增【3.1零信任架构方法的变化】和【4.5面向公众或客户提供服务的企业】两节。其中,3.1节主要介绍了ZTA的三种实现方式:基于增强身份治理的ZTA、采用微分隔的ZTA、采用网络基础架构和SDP的ZTA。在实践时,企业可以结合自身情况采用一种或多种结合作为策略的主要驱动因素完成整体设计。4.5节则是对部署场景/用例的补充。
另外,Draft2中对【2.1零信任的宗旨】进行了详细的修正,涉及多条修改,并新增一条原则(从6条增加到7条):企业应尽可能收集有关网络基础架构和通信现状的信息,并利用这些信息改善安全姿态(security posture)。企业应该收集有关网络流量和访问请求的数据,然后使用这些数据来改进策略的创建和实施。此数据还可用于为来自主体的访问请求提供上下文。Draft2针对Draft1中【3.3.1支持ZTA的网络要求】,新增对于基础架构扩展性的要求(PE、PA和PEP都是关键组成);针对Draft1中【5.7在ZTA管理中使用非人实体】,描述了误报的影响,提出可定期重新调整分析来纠正错误的决策并改进决策过程;针对Draft1中【7.3.2识别企业拥有的资产】,新增加对影子资产的描述。总之,Draft2中还新添多处细节内容,这里不再一一赘述,新增内容请参照下文详细对比部分。特别的,Draft2新增7篇参考文献,为[BCORE]、[FIPS199]、[IBNVN]、[NISTIR8062]、[NISTPRIV]、[SDNBOOK]、[SP800-63-3]。
第二部分、修改部分
Draft2针对Draft1的主要修改包括读者群体、受益群体、ZT和ZTA定义区分、保护对象、适用范围、向ZTA过渡前提等方面:
【读者群体】
读者群体由企业网络架构师修改为企业安全架构师。
【受益群体】
零信任/零信任架构的受益群体从Draft1中的“任何拥有具有多个资源的大型网络的组织”修改为“任何组织”。
【ZT和ZTA定义区分】
Draft1中未对ZT和ZTA明确定义,Draft2中对Draft1对于ZTA的定义进修改,明确ZT和ZTA的定义。其中ZT主要指概念和思想,而ZTA则主要指利用ZT的企业网络安全规划,包括组件关系、工作流规划和访问策略。
【保护对象】
Draft2删除了Draft1中“零信任是一种侧重于数据保护的体系架构方法”一条。在Draft2中修改为:安全防护应该围绕着“资产(数据、计算资产和应用等)”进行,不再只集中于对于数据的保护。
【适用范围】
Draft2对Draft 2.1零信任的宗旨修改补充:零信任的宗旨适用于在一个组织内部或与一个或多个合作伙伴组织协作完成的工作,不适用于面向公众或客户的业务流程。组织不能将内部的安全策略强加给外部参与者(例如,客户或普通互联网用户)。
【向ZTA过渡】
在Draft1中提出向“ZTA过渡需要过程,需要全面的技术替换才可实现。”在Draft2中修改为“向ZTA过渡是关于组织如何评估其任务中的风险的过程,而不仅仅是简单地通过全面的技术替换就能实现。”除必要的技术替代外还需要重视风险评估。
在上文主要的修正之外,Draft2也对标准中的措辞进行矫正,一些主要的矫正下表所示,更为细节请参照下文详细对比部分。
全文详细对比如下。
NIST《零信任架构》标准草案第2版全文对比
Abstract摘要
摘要中主要对前三句进行了修改。主要对零信任和零信任架构的定义进行修正和区分。在草案2中去掉了strategy的概念。
草案1:【Zero Trust is the term for an evolving set of network security paradigms that move network defenses from wide network perimeters to narrowly focusing on individual or small groups of resources.A Zero Trust Architecture (ZTA) strategy is one where there is no implicit trust granted to systems based on their physical or network location (i.e., local area networks vs. the Internet). Access to data resources is granted when the resource is required, and authentication (both user and device) is performed before the connection is established.】
零信任(Zero Trust)是一种不断发展的网络安全范式的术语,这种范式将网络防御从广泛的网络边界转移到仅关注个体或一小部分资源。零信任体系结构(ZTA)战略是指不存在基于系统的物理或网络位置(即局域网与因特网)而授予系统隐式信任的战略。当需要资源时,授予对数据资源的访问权,并在建立连接之前执行身份认证(用户和设备)。
草案2:【Zero trust (ZT) is the term for an evolving set of cybersecurity paradigms that move network defenses from static, network-based perimeters to focus on users, assets, and resources.A zero trust architecture (ZTA) uses zero trust principles to plan enterprise infrastructure and workflows. Zero trust assumes there is no implicit trust granted to assets or user accounts based solely on their physical or network location (i.e., local area networks versus the internet). Authentication and authorization (both user and device) are discrete functions performed before a session to an enterprise resource is established.】
零信任(Zero trust,ZT)是一种不断发展的网络安全范式的术语,将网络防御从静态的、基于网络边界的防护转移到关注用户、资产和资源。零信任体系结构(ZTA)使用零信任原则来规划企业基础架构和工作流。零信任假定不存在仅仅基于物理或网络位置(即局域网与互联网)即授予资产或用户帐户的隐式信任。身份认证和授权(用户和设备)是在建立与企业资源的会话之前执行的独立功能。
Audience读者群体
草案1中的【enterprise network architects】修改为草案2中的【enterprise security architects.】:即企业网络架构师,修改为企业安全架构师。
草案1中的【deploy ZTA concepts to an enterprise network.】修改为草案2中【deploy zero trust security concepts to an enterprise environment.】即:将ZTA概念部署到企业网络修改为将零信任安全概念部署到企业环境。
草案1中的【gain insight into ZTA from this document.】修改为草案2中的【gain insight into zero trust and ZTA from this document】即:将从本文档了解零信任架构修改为将从本文档了解零信任和零信任架构。
Note to Reviewers
草案1中的【logical components of network infrastructure using a ZTA strategy.】修改为草案2中的【logical architectural components to develop and support a ZTA.】即:将“采用ZTA战略的网络架构的逻辑组件”修改为“开发和支持ZTA的逻辑架构组件”。
1 Introduction
草案1中274行,第一段最后增加一句:【Perimeter-based network security has also been shown to be insufficient since once attackers breach the perimeter, further lateral movement is unhindered.】即增加说明:【基于边界的网络安全也被证明是不够的,因为一旦攻击者突破边界,进一步的横向移动便会畅通无阻。】
草案1中275行,【a new way to plan enterprise network security known as Zero Trust Architecture (ZTA).】修改为【the development of a new model for cybersecurity principles and network security known as “zero trust” (ZT).】即:【一种新的企业网络安全规划方法称为零信任架构(ZTA)。】修改为【网络安全原则和网络安全新模式的发展称为“零信任”(ZT)。】
草案1中276行,【A ZTA approach】修改为【A ZT approach】。
草案1中277行,对企业资产进行了定义【all enterprise assets, such as devices, infrastructure, and users.】,企业的资产是包括设备、基础架构和用户。
草案1中277行,【ZTA assumes the network is hostile】修改为【Zero trust security models assume that an attacker is present on the network 】即:将【ZTA假设网络是充满威胁的】修改为【零信任安全模型假设网络上存在攻击者】。
草案1中278行,【no more secure】修改为【no more trustworthy】即:【不再安全】修改为【不再值得信赖】。
草案1中281行,【In ZTA】修改为【In zero trust】。
草案1中282行,【minimizing access to resources to only those who are validated as needing access and continuouslyauthenticating the identity and security posture of each access request.】修改为【minimizing access to resources(such as data and compute resources and applications) to only thoseusers and asset identified as needing access as well as continuallyauthenticating and authorizing the identity and security posture of each access request.”即【尽可能减少对资源的访问,只允许那些经过证实需要访问的人访问,并对每个访问请求的身份和安全姿态进行持续认证。】修改为【尽可能减少对资源(如数据、计算资源和应用)的访问,只允许那些被确定为需要访问的用户和资产访问,并对每个访问请求的身份和安全姿态进行持续认证和授权。】这其中对资源的范围进行了说明,资源包括数据、计算资源和应用,另外强调不止需要authenticating还需要authorizing。
草案1中284行,开头增加一句【A zero trust architecture (ZTA) is an enterprise cybersecurity strategy that is based on zero trust principles and designed to prevent data breaches and limit internal lateral movement.】即:【零信任架构(ZTA)是一种基于零信任原则的企业网络安全战略,旨在防止数据泄露和限制内部横向移动。】这里对ZT和ZTA的关系进行了说明。
草案1中286行,【migrate to a ZTA-centered network infrastructure】修改为【migrate to a zero trust design approach to network infrastructure】即:【迁移到以ZTA为中心的网络基础架构】修改为【迁移到网络基础架构的零信任设计方法】。
草案1中288行,【ZTA】更正为【ZT】。
草案1中288行,【network infrastructure design】修改为【network infrastructure and system design】。
草案1中290行,明确参考了[FIPS199]。
草案1中290行,【Transitioning to ZTA is a journey and cannot be accomplished without a wholesale replacement of technology.】修改为【Transitioning to ZTA is a journey concerning how an organization evaluates risk in its mission and cannot simply be accomplished with a wholesale replacement of technology.】即:【向ZTA过渡是一个过程,如果没有全面的技术替换,就无法实现】修改为【向ZTA过渡是关于组织如何评估其任务中的风险的过程,而不仅仅是简单地通过全面的技术替换就能实现。】即强调ZTA的实现不是一蹴而就的,这个过渡过程不是说堆砌一堆新技术去替代原来用技术就能成功实践,还需要关注组织自身进行风险评估的方式。
草案1中293行,【technology solutions that protect its data assets and business functions.】修改为【technology solutions that protect their data assets and business functions by use case.】即【保护其数据资产和业务功能的技术解决方案】修改为【通过用例保护其数据资产和业务功能的技术解决方案】。
草案1中295行,【hybrid Zero Trust/Legacy mode】修改为【hybrid zero trust/perimeter-based mode】即:【零信任/传统模式的混合模式】修改为【零信任/基于边界模式的混合模式】。
草案1中297行,【effective information security】修改为【comprehensive information security】,即:【有效的信息安全】修改为【全面的信息安全】。
草案1中298行,【complemented with existing cybersecurity policies】修改为【balanced with existing cybersecurity policies】即:【与现有的网络安全测略互补】修改为【与现有的网络安全策略相平衡】。
草案1中299行,【general cybersecurity】修改为【best practices】,即【一般的网络安全】修改为【最佳实践】。
1.1 History of Zero Trust Efforts Related to Federal Agencies
草案1中302行,1.1节名从“背景”调整为“与联邦机构有关的零信任发展历史”。
草案1中304行,增加一句【The Defense Information Systems Agency (DISA) and the Department of Defense published their work on a more secure enterprise strategy dubbed “black core” [BCORE]. Black core involved moving from a perimeter-based security model to one that focused on the security of individual transactions.】即增加【国防信息系统局(DISA)和国防部(DOD)公布了他们在更安全的企业战略方面的工作,称之为“black core”[BCORE]。Black core中涉及了从基于边界的安全模型转移到关注单个事务安全的模型。】
草案1中304行,【The work of the Jericho Forum publicized the idea of limiting implicit trust based on network location and the limitations of relying on static defenses [JERICHO].】修改为【The work of the Jericho Forum in 1994 publicized the idea of de-perimeterization—limiting implicit trust based on network location and the limitations of relying on single, static defenses over a large network segment[JERICHO].】,即【Jericho论坛的工作公开了限制基于网络位置赋予隐式信任的思想和依赖静态防御的局限性[Jericho]。】修改为【1994年Jericho论坛的工作公开了去边界化的思想—限制基于网络位置默认的信任,以及在一张大网上依赖单一的、静态的防御的局限性[JERICHO]】。
草案1中307行,去掉(now at Palo Alto Networks).
草案1中308行,去掉【This work included key conceptsand a zero trust network architecture model that improved upon the conceptsdiscussed in the Jericho Forum.】,即去掉【这项工作包括关键概念和零信任网络架构模型,该模型改进了在Jericho论坛上讨论的概念。】
草案1中309行,增加【Zero trust then became the term used to describe various cybersecurity solutions that moved security away from implied trust based on network location and instead focused on evaluating truston a per-transaction basis. Both private industry and higher education have also undergone this evolution from perimeter-based security to a security strategy based on zero trust principles.】即【零信任后来成为一个术语,用来描述各种网络安全解决方案,这些解决方案将安全性从基于网络位置的默认信任转移到基于每个事务的信任评估上来。私人企业和高等教育行业也经历了从基于边界的安全到基于零信任原则的安全战略的演变。】
草案1中320行,增加【to a “need to access” basis to mitigate data exposure due to compromised accounts, attackers monitoring anetwork, and other threats.】即【“需要访问”为基础,减轻由于帐户受损、攻击者监视网络和其他威胁而导致的数据暴露。】
2 Zero Trust Basics
草案1中340行,第二章的标题【Zero Trust Network Architecture】修改为【Zero Trust Basics】。
草案1中341行,增加一句【Zero trust is a cybersecurity paradigm focused on resource protection and the premise that trust is never granted implicitly but must be continually evaluated.】即【零信任是一种以资源保护为核心的网络安全范式,其前提是信任从来不是隐式授予的,而是必须进行持续评估。】
草案1中341行,【network/data security】修改为【enterprise resource and data security】,即【网络/数据安全】修改为【企业资源和数据安全】。
草案1中342行,【identity】修改为【identity (person and non-person entities)】对identity进行了明确,包括人和非人的实体。
草案1中343行,删除【Zero trustis an architectural approach that is focused on data protection.】。
草案1中344行,【The initial focus should be on restricting resource access to those with a “need to know.】修改为【The initial focus should be on restricting resources to those with a need to accessand grant only the minimum privileges (e.g., read, write,delete) needed to perform the mission.】即将【需要知悉】修改为【需要访问并仅授予执行任务所需的最小权限(如读取、修改、删除)】。
草案1中350行,增加【(the TICs and perimeter firewalls) and cannot protect users outside of the perimeter(e.g., remote workers, cloud-based services).】即【无法保护边界外的用户(例如,远程工作者、基于云的服务)】,表明TIC(Trusted Internet Connections,可信互联网连接)和边界防火墙在在检测和阻止来自网络内部的攻击方面用处不大并且也无法保护边界外的用户(例如,远程工作者、基于云的服务)。
草案1中351行,在第一版草案的ZTA的定义,在第二版中修改为ZT和ZTA的定义。【Zero Trust Architecture (ZTA) provides a collection of concepts, ideas, and component relationships (architectures) designed to eliminate the uncertainty in enforcing accurate access decisions in information systems and services.】修改为【Zero trust (ZT) provides a collection of concepts and ideas designed to reduce the uncertainty in enforcing accurate, per-request access decisions in information systems and services in the face of a network viewed as compromised. Zero trust architecture (ZTA) is an enterprise’s cybersecurity plan that utilizes zero trust concepts and encompasses component relationships, workflow planning, and access policies. Therefore, a zero trust enterprise is the network infrastructure (physical and virtual) and operational policies that are in place for an enterprise as a product of a zero trust architecture plan.】即【零信任体系结构(ZTA)提供了一系列概念、思想和组件关系(体系架构),旨在消除在信息系统和服务中实施准确访问决策时的不确定性。】修改为【零信任(Zero trust,ZT)提供了一系列概念和思想,旨在面对被视为受损的网络时,减少在信息系统和服务中执行准确的、按请求访问决策时的不确定性。零信任架构(ZTA)是一种企业网络安全规划,它利用零信任概念,并囊括其组件关系、工作流规划与访问策略。因此,零信任企业作为零信任架构规划的产物,是指为企业准备的(物理和虚拟的)网络基础设施及操作策略。】
草案1中355行,增加一段【An enterprise decides to adopt zero trust as its cybersecurity foundation and generate a zero trust architecture as a plan developed with zero trust principles in mind. This plan is then deployed to produce a zero trust environment for use in the enterprise.】即【一个企业决定采用零信任作为它的网络安全基础,并将零信任架构作为一个以零信任原则开发的计划。然后部署此计划以生成一个零信任环境,供企业使用。】
草案1中355行,【which is to eliminate unauthorized access to data and services】修改为【which is the goal to prevent unauthorized access to data and services】,即【这是为了消除对数据和服务的未经授权的访问】修改为【这是为了防止未经授权访问数据和服务】。
草案1中357行,【subjects (user/machine)】修改为【subjects(combination of user, application, and device)】即原本的主体指用户/机器,修改为主体是用户、应用和设备的组合。
草案1中362行,【minimizing temporal delays innetwork authentication mechanisms.】修改为【minimizing temporal delays in authentication mechanisms.】即【最小化网络认证机制中的时间延迟】修改为【最小化认证机制中的时间延迟】,去掉了网络。
草案1中370行,【trustworthy】修改为【authentic】,即【值得信赖的】修改为【真实的】。
草案1中372行,【Can the system remove sufficient doubt about the user’s true identity? Is the user justified in their access request? Is the device used for the request trustworthy?】修改为【What is the level of confidence about the user’s identity for this unique request? Is access to the resource allowable given the level of confidence in the user’s identity? Does the device used for the request have the proper security posture? Are there other factors that should be considered and that change the confidence level (e.g.,time, location of subject, subject’s security posture)?】即【系统能消除对用户真实身份的足够怀疑吗?用户的访问请求是否合理?用于请求的设备是否可信?】修改为【对于这个唯一的请求,用户的身份的可信度是多少?考虑到对用户身份的信任程度,是否允许访问资源?用于请求的设备是否具有正确的安全姿态?是否有其他因素需要考虑,这些因素可能改变可信度(如时间、主体位置、主体安全姿态)?】
草案1中374行,【Overall,enterprises need to develop risk-based policies for resource access and set up a system to ensure that these policies are executed correctly.】修改为【Overall, enterprises need to develop and maintain dynamic risk-based policies for resource access and set up a system to ensure that these policies are enforced correctly and consistently.】即【总的来说,企业需要为资源访问制定基于风险的策略,并建立一个系统来确保这些策略的正确执行】修改为【总的来说,企业需要为资源访问制定和维护动态的基于风险的策略,并建立一个系统来确保这些策略得到正确和一致的执行。】
草案1中377行,【(i.e.,logging into a system)】修改为【(logging into an asset)】,即【登录系统】修改为【登录到资产】。
草案1中382行,【all the cleared passengers have a common trust level.】修改为【all the cleared passengers are considered trusted.】即【所有通过检查的乘客都有一个共同的信任级别。】修改为【所有通过检查的乘客都被认为是可信的。】
草案1中388行,【“Zero Trust Architecture provides technology and capabilities to allow the PDP/PEPs to move closer to the resource. The idea is to authenticate and authorizeevery single flow in the network from actor (or application)to data.】修改为【Zero trust provides a set of principles and concepts around moving the PDP/PEPs closer tothe resource. The idea is toexplicitly authenticate and authorizeall users, devices, applications, and workflows that make up the enterprise.】即【零信任体系结构提供了技术和能力,允许PDP/PEP更接近资源。其思想是对网络中从参与者(或应用)到数据的每个流进行身份验证和授权。】修改为【零信任提供了一套原则和概念,使PDP/PEP更接近资源。其思想是明确地验证和授权组成企业的所有用户、设备、应用程序和工作流。】
2.1 Tenets of Zero Trust Architecture
草案1中391行,2.1题目修改为【Tenets of Zero Trust】,零信任的宗旨。
草案1中394行,增加“as part ofthe functional capabilities of a ZTA.”,即一些微分段的方案依然将边界防护作为“零信任功能的一部分”。
草案1中396行,增加【These tenets are the ideal goal, though it must be acknowledged that not all tenets may be fully implemented in their purest form for a given strategy.】即【这些宗旨是理想目标,尽管必须承认,并非所有的宗旨都可以在给定的战略中以其最纯粹的形式得到充分实现。】
草案1中400行,增加“software as a service (SaaS)”。
草案1中409行,【All communication should be done in a secure manner (i.e., encrypted and authenticated).】修改为【All communication should be done in the most secure manner available, protect confidentiality and integrity, and provide source authentication.】,即【所有通信应以安全的方式进行(即加密和认证)。】修改为【所有通信应以最安全的方式进行,保护机密性和完整性,并提供源身份认证。】
草案1中413行,【before initiating a connection with a resource.”修改为“before initiating a session or performing a transaction with a resource.】即【在启动与资源的连接之前】修改为【启动会话或使用资源执行事务之前。】
草案1中413行,【authentication】修改为【authentication andauthorization】,即变为【认证和授权】。
草案1中416行,【including the observable state of user identity and the requesting system】修改为【including the observable state of client identity, application, and the requesting asset】,即【包括用户身份和请求系统的的可观察状态】修改为【包括客户身份、应用和请求资产的可观察状态】,扩展了影响动态策略的因素。
草案1中417行【who its members are】修改为【who its members are (or ability to authenticate users from a federated community),】即【其成员是谁】修改为【其成员是谁(或对来自联邦的用户进行身份认证的能力)】。
草案1中419行【assigned by the enterprise to that account.】修改为【assigned by the enterprise to that account or artifacts to authenticate automated tasks.】即【由企业分配给该帐户】修改为【由企业分配给该帐户或工件以认证自动化任务】。
草案1中421行,对于请求资产的状态,除软件版本、网络位置等,增加了【time/date of request】。
草案1中423行,【Policy is the set of attributes an organization assigns to a user, dataasset, or application.】修改为【Policy is the set of access rules based on attributes that an organization assigns to a user, data asset,or application.】即【策略是组织分配给用户、数据资产或应用的一组属性。】修改为【策略是基于组织分配给用户、数据资产或应用的属性的访问规则集。】对于策略修正了定义。
草案1中425行,【Resource access policies】修改为【Resource access and actionpermission policies】即【资源访问策略】修改为【资源访问和操作权限策略】。
草案1中430行,增加一句【No device is inherently trusted. Here, “most secure state possible” means that thedevice is in the most practicable secure state and still performs the actions required for the mission.】修改为【没有设备是天生可信的。这里,“可能的最安全状态”是指设备处于最可行的安全状态,并且仍然执行任务所需的操作。】
草案1中430行,【establish a Continuing Diagnostics and Mitigation (CDM) program to monitor the state ofsystems and apply patches/fixes as needed】修改为【establish a CDM or similar system to monitorthe state of devices and applications and should apply patches/fixes as needed.】即【建立持续诊断和缓解(CDM)计划,以监控系统状态,并根据需要应用补丁/修复程序】修改为【建立一个CDM或类似的系统来监控设备和应用的状态,并根据需要应用补丁/修复程序。】说明不限定必须是CDM系统。
草案1中432行,【Systems that are discovered to be subverted,vulnerable, and/ornon-enterprise-owned may be treated differently】修改为【Devices that are discovered to be subverted,have known vulnerabilities,and/orare not managed by the enterprise may be treated differently】即【被发现为被颠覆、易受攻击和/或非企业所有的系统可能会受到不同的对待】修改为【发现被颠覆、具有已知漏洞和/或不受企业管理的设备可能会受到不同的对待】修订后的描述更为准确,比如,企业自己的设备也不见得完全受企业管理,这些设备是可能非受控的。
草案1中434行,【system】修改为【device】。
草案1中435行,增加【This may also apply to associated devices (e.g., personally owned devices) that may beallowed to access some resources but not others. This, too, requires a robust monitoring and reporting system in place to provide actionable data about the current state of enterprise resources.】即【这也可能适用于允许访问某些资源但不允许访问其他资源的关联设备(例如,个人拥有的设备)。这也需要一个强大的监控和报告系统来提供关于企业资源当前状态的可操作数据。】
草案1中436行,【User authentication】修改为【All resource authentication and authorization】即【用户身份认证】修改为【所有资源身份认证和授权】。
草案1中437行,【continuously authenticating.】修改为【continually reevaluating trust in ongoing communication.】即【持续认证】修改为【在通信中进行持续信任评估。】
草案1中438行,【An enterprise implementing a ZTA strategy has a user provisioning system in place and uses the system to authorize access to resources.】修改为【An enterprise implementing a ZTA would be expected to have Identity, Credential, and Access Management (ICAM) and asset management systems in place.】即【实施ZTA战略的企业有一个用户供应系统,并使用该系统授权对资源的访问。】修改为【实现ZTA的企业应该具有身份、凭证和访问管理(ICAM)以及资产管理系统。】
草案1中441行【Continuous monitoring and re-authentication occur throughout user interaction】修改为【Continuous monitoring with possible re-authentication and reauthorization occurs throughout user interaction】即【在用户交互过程中,会持续监视和重新认证】修改为【在整个用户交互过程中,会持续监视,可能的重新认证和重新授权。】
草案1中443行,对于策略增加了【anomalous user activity detected】即【检测到异常用户活动】。
草案1中445行,增加【The enterprise collects as much information as possible about the current state of network infrastructure and communications and uses it to improve its security posture. An enterprise should collect data about network traffic and access requests, which is then used to improve policy creation and enforcement. This data can also be used to provide context for access requests from subjects (see Section 3.3.1).】即【企业尽可能收集有关网络基础架构和通信现状的信息,并利用这些信息改善其安全姿态。企业应该收集有关网络流量和访问请求的数据,然后使用这些数据来改进策略的创建和实施。此数据还可用于为来自主体的访问请求提供上下文(请参阅第3.3.1节)。】
草案1中446行,“network ID”修改为““user identification (ID)”。
草案1中448行,删除【or someother identification.】。
草案1中448行,增加【These tenets apply to work done within an organization or in collaboration with one or more partner organizations and not to public or consumer-facing business processes. An organization cannot impose internal policies on external actors(e.g., customers or general internet users).】即【此类宗旨适用于在一个组织内或与一个或多个合作伙伴组织协作完成的工作,而不适用于面向公众或消费者的业务流程。组织不能将内部政策强加给外部参与者(例如,客户或普通互联网用户)】。
2.2 A Zero Trust View of a Network
2.2.1 Assumptions for Enterprise-Owned Network Infrastructure
草案1中457行,【The enterprise private network is not trustworthy.】修改为【The entire enterprise private network is not considered an implicit trust zone.】即【企业专网不值得信赖。】修改为【整个企业专网不被视为隐式信任区。】
草案1中459行,【in a secure manner】修改为【in the most secure manner available】,即【以安全的方式】修改为【以最安全的方式】。
草案1中466行,【 No deviceis inherently trusted.】修改为【No resource is inherently trusted.】即【没有设备是天生可信的。】修改为【没有资源是天生可信的。】
草案1中466行,【Every device must authenticate itself (either to resource or PEP)】修改为【Every asset must have its security posture evaluated via a PEP】即【每个设备都必须对自身进行身份验证(对resource或PEP)】修改为【每个资产都必须通过PEP评估其安全姿态】。
草案1中469行,【provide a higher trust score than the same request】修改为【provide a confidence level higher than the same request】即【提供比同一请求更高的信任分数】修改为【提供高于同一请求的信任程度】。
2.2.2 Assumptions for Non-Enterprise-Owned Network Infrastructure
草案1中475行,【The enterprise must be able to monitor, configure, and patch any system, but any system may rely on the local (i.e., non-enterprise) network for basic connectivity and network services (e.g., DNS, etc.).】修改为【Enterprise-owned or -managed assets may need to utilize the local(i.e., nonenterprise) network for basic connectivity and network services(e.g., DNS resolution).】即【企业必须能够监视、配置和修补任何系统,但任何系统都可能依赖本地(即非企业)网络进行基本连接和网络服务(如DNS等)】修改为【企业拥有或管理的资产可能需要利用本地(即非企业)网络进行基本连接和网络服务(如DNS解析)。】
草案1中480行,【All connection requests should be authenticated, and all traffic should be encrypted】修改为【All connection requests should be authenticated and authorized, and all communications should be done in the most secure manner possible (i.e., provide confidentiality, integrity protection,and source authentication).】即【所有连接请求都应该经过身份认证,所有通信都应该加密】修改为【所有连接请求都应经过身份认证和授权,所有通信都应尽可能以最安全的方式完成(即提供机密性、完整性保护和源身份认证)。】
3. Logical Components of Zero Trust Architecture
草案1中485行,第三章的标题【Zero Trust Architecture Logical Components】修改为【Logical Components of Zero Trust Architecture】。
草案1中490行,增加一句【The ZTA logical components use a separate control plane to communicate, while application data is communicated on a data plane (see Section 3.4).】即【ZTA逻辑组件使用单独的控制平面进行通信,而应用数据在数据平面上进行通信(见第3.4节)。】
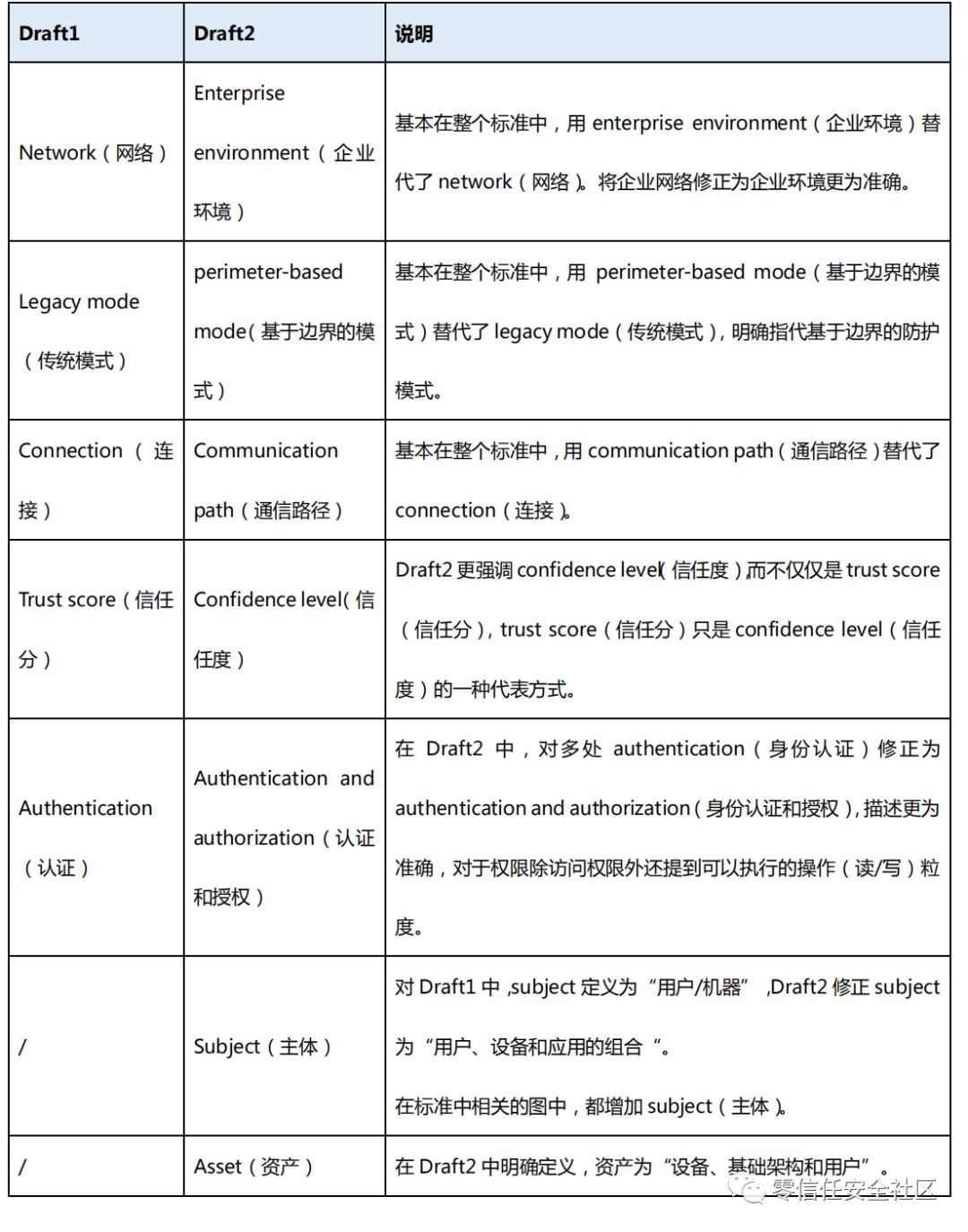
草案1中492行,针对图2“零信任核心逻辑组件图”进行了修正,主要包含四处修正:1)policy engine和policy administrator合并称为“PDP”;2)设备明确为system;3)增加subject一项;3)外侧增加一项,Activity logs。
(草案2中)零信任核心逻辑组件图
草案1中497行,【grant accessto a resource for a given client or subject.】修改为【grant access to a resource for a givensubject.】去掉了client。
草案1中498行,【external sources (e.g., IP blacklists, threat intelligence services)】修改为【external sources (e.g.,CDM systems, threat intelligence services described below)】在第三方能力组件中增加了CDM系统。
草案1中499行,【to decide togrant or deny access to the resource.】修改为【to grant,deny,or revoke access to the resource.】增加了对访问处理的“”撤销(revoke)”决策。
草案1中503行,【This component is responsible for establishing the connection between aclient and a resource.】修改为【This component is responsible for establishing and/orshutting down the communication path betweena subject and a resource.】即,增加了shutting down(关闭),表达更准确;同时连接是在subject(主体)和resource(资源)之间的,而不是client(客户端)和resource(资源)之间。
草案1中506,【connection(连接)】修改为【session(进程)】。
草案1中509,【the connection(连接)】修改为【the communication path(通信路径)】。
草案1中516,【theconnection(连接)】修改为【the communication path(通信路径)】。
草案1中516行,增加【Beyond the PEP is the implicit trust zone (see Section 2) hosting the enterprise resource.】即【在PEP之外是托管企业资源的隐式信任区域(请参阅第2节)。】
草案1中528行,【(e.g. FISMA,HIPAA, PCI- DSS, etc.).】修改为【e.g., FISMA, healthcare orfinancial industry information security requirements)】,去掉了PCI- DSS,使用更为通用的行业安全要求来表达。
草案1中530行,对于Threat Intelligence Feed(s),将【This system provides information from outside sources that help the Policy Engine make access decisions.】修改为【This provides information from internal or external sources that help the policy engine make access decisions】即,讲过信息源从外部源,扩展为内部或外部源头;指出威胁情报可能来自于外部也可能来自内部。
草案1中533行,【This also includes DNS blacklists, discovered malware,or command and control systems】修改为【This also includes blacklists, newly identified malware, and reported attacks to other assets】,对于【DNS黑名单】修改为【黑名单】,对于【发现的恶意软件】修改为【新识别的恶意软件】,删除【command and control system】,增加【报告的对其他资产的攻击】。
草案1中536行,数据访问策略,【policies about data access created by the enterprise around enterprise resources.】修改为【policies about access to enterprise resources.】即“关于企业围绕企业资源创建的数据访问的策略。”修改为“有关访问企业资源的策略。”,强调资源层面,而不是数据。
草案1中540行,【Theseroles and access rules should be based onuser roles and the mission needs of the organization.】修改为【Thesepolicies shouldbe based on the definedmission roles and needs of the organization.】即【这些角色和访问规则应基于用户角色和组织的任务需求】修改为【这些策略应以本组织确定的任务角色和需要为基础。】
草案1中543行,【actors】修改为【subjects】。
草案1中545行,增加一句【This could also be a PKI that is not built upon X.509 certificates.】即【这也可能是不是建立在X.509证书上的PKI。】
草案1中547行,ID管理系统,【identity records】修改为【identity records (e.g., lightweight directory access protocol (LDAP) server)】,对身份记录进一步说明为【例如,轻量级目录访问协议(LDAP)服务器】。
草案1中550行,增加【This system may be part of a larger federated community and may include nonenterprise employees or links to nonenterprise assets for collaboration.】即【该系统可能是一个更大的联邦社区的一部分,可能包括非企业员工或链接到非企业资产进行协作。】ID管理系统,可能会扩展到联邦身份的概念。
草案1中551行,增加一条对于网络和系统活动日志的内容【Network and system activity logs: This is the enterprise system that aggregates asset logs, network traffic, resource access actions, and other events that provide real-time (or near-real-time) feedback on the security posture of enterprise information systems.】即【网络和系统活动日志:这是一个企业系统,它聚合了资产日志、网络流量、资源访问操作和其他事件,这些事件提供关于企业信息系统安全姿态的实时(或接近实时)反馈。】
草案1中551行,修改SIEM系统的定义【Security information and event management (SIEM) system: This collects security- centric information for later analysis. This data is then used to refine policies and warn of possible attacks against enterprise assets.】即【安全信息和事件管理(SIEM)系统:它收集以安全为中心的信息以供以后分析。然后,这些数据将用于完善策略并警告可能对企业资产发起的攻击。”】
3.1 Variations of Zero Trust Architecture Approaches(新增)
新增一节【3.1 Variations of Zero Trust Architecture Approaches】即【零信任架构方法的变化】。
【There are several ways that an enterprisecan enact a ZTA for workflows. These approaches vary in the components used and in the main source of policy rules for an organization. Each approach implements all the tenets of ZT (see Section 2.1) but may use one or two (or one component) as the main driver of policies. The approaches include enhanced identity governance–driven, logical micro-segmentation via next-generation firewalls (NGFWs), and network-based segmentation.】即【企业可以通过多种方式为工作流制定ZTA。这些方法因使用的组件和组织的策略规则的主要来源而异。每种方法都达成了ZT的全部宗旨(见第2.1节),但可以使用一个或两个(或一个组件)作为策略的主要驱动因素。这些方法包括增强的身份治理驱动、通过下一代防火墙(NGFWs)进行逻辑微分段以及基于网络的分段。】
【Certain approaches lend themselves to some use cases more than others. An organization looking to develop a ZTA for its enterprise may find that its chosen use case and existing policies point to one approach over others. That does not mean the other approaches would not work but rather that other approaches may be more difficult to implement and may require more fundamental changes to how the enterprise currently conducts business flows.】即【对于某些用例来说,某些方法会显得比其他方法更适合。为企业研发ZTA的组织部门可能会发现,其选择的用例和现有策略指向某一种特定方法而不是其他方法。这并不意味着其他方法不起作用,而是意味着其他方法可能更难实施,并且可能需要对企业当前如何进行业务流造成更根本的更改。】
3.1.1 ZTA Using Enhanced Identity Governance
标题:使用增强身份治理的ZTA。
【The enhanced identity governance approach to developing a ZTA uses the identity of actors as the key component of policy creation. If it were not for subjects requesting access to enterprise resources, there would be no need to create access polices. For this approach, enterprise resource access policies are based on identity and assigned attributes. The primary requirement for resource access is based on the access privileges granted to the given subject. Other factors such as device used, asset status, and environmental factors may alter the final confidence level calculation (and ultimate access authorization) or tailor the result in some way, such as granting only partial access to a given data source based on network location. Individual resources or PEP components protecting the resource must have a way to forward requests to a policy engine service or authenticate the subject and approve the request before granting access.】即【实现ZTA的增强身份治理方法使用参与者身份作为策略创建的关键组件。如果不是针对请求访问企业资源的主体,则无需创建访问策略。对于这种方法,企业资源访问策略基于身份和分配的属性。资源访问的主要要求基于授予给定主体的访问权限。其他因素,如使用的设备、资产状态和环境因素,可以改变最终信任程度算(和最终访问授权),或者以某种方式调整结果,例如基于网络位置仅授予对给定数据源的部分访问。保护资源的单个资源或PEP组件必须具有将请求转发到策略引擎服务或认证主体并在授予访问权限之前批准请求的方法。】
【Enhanced identity governance-based approaches for enterprises are often found using an open network model or an enterprise network with visitor access or frequent nonenterprise devices on the network (such as with the use case in Section 4.3 below). Network access is initially granted to all assets with access to resources that are restricted to identities with the appropriate access privileges. The identity-driven approach works well with the resource portal model since device identity and status provide secondary support data toaccess decisions. Other models work as well, depending on policies in place.】即【针对企业的基于增强身份治理的方法通常使用开放网络模型或有访客访问的企业网络或非企业设备常接入网络的情况(如下面第4.3节中的用例)。网络访问最初被授予对资源具有访问权限的所有资产,这些资源仅限于具有适当访问权限的身份。身份驱动的方法与资源门户模型很好地配合,因为设备身份和状态为访问决策提供辅助支持数据。其他模式也可以工作,这取决于现有的策略。】
3.1.2 ZTA Using Micro-Segmentation
标题:使用微分段的ZTA。
【An enterprise may choose to implement a ZTA based on placing individual or groups of resources on its own network segment protected by agateway security component. In this approach, the enterprise places NGFWs orgateway devices to act as PEPs protecting each resource or group of resources.These gateway devices dynamically grant access to individual requests from aclient asset. Depending on the model, the gateway may be the sole PEP componentor part of a multipart PEP consisting of the gateway and client-side agent (seeSection 3.2.1).】即【企业可以选择通过将单个或资源组部署在由网关安全组件保护的自身网段上来实现ZTA。在这种方法中,企业放置NGFWs或网关设备作为PEP来保护每个资源或资源组。这些网关设备为来自客户端资产的每个请求动态的授予访问权。根据模型的不同,网关可以是唯一的PEP组件,也可以是由网关和客户端代理组成的PEP的一部分(见第3.2.1节)。】
【This approach applies to a variety of use cases and deployment models as the protecting device acts as the PEP, with management of said devices acting as the PE/PA component. This approach requires an identity governance program to fully function but relies on the gateway components to act as the PEP that shields resources from unauthorized access and/or discovery.】即【此方法适用于各种用例和部署模型,因为保护设备充当PEP,而管理所述设备充当PE/PA组件。这种方法需要一个身份治理程序来完全发挥作用,但依赖于网关组件作为PEP,以保护资源免受未经授权的访问和/或发现。】
【The key necessity to this approach is that the PEP components are managed and should be able to react and reconfigure as needed to respond to threats or change in the workflow. It is possible to implement some features of a micro-segmented enterprise by using less advanced gateway devices and even stateless firewalls, but the administration cost and difficulty to quickly adapt to changes make this a very poor choice.】即【这种方法的关键必要性在于,PEP组件是受管理的,并且应该能够根据需要进行响应和重新配置,以响应工作流中的威胁或更改。虽然通过使用不太先进的网关设备甚至无状态防火墙,可以实现微分隔企业的某些功能,但管理成本和快速适应变化的困难使这成为一个非常糟糕的选择。】
3.1.3 ZTA Using Network Infrastructure and Software Defined Perimeters
标题:使用网络基础架构和软件定义边界的ZTA。
【The third approach uses the network infrastructure to implement a ZTA. The ZT implementation could be achieved by using an overlay network (i.e.,layer 7 but also could be set up lower of the ISO network stack). These approaches are sometimes referred to as software defined perimeter (SDP) approaches and frequently include concepts from SDN [SDNBOOK] and intent-based networking(IBN) [IBNVN]. In this approach, the PA acts as the network controller that setsup and reconfigures the network based on the decisions made by the PE. The clients continue to request access via PEPs, which are managed by the PA component.】即【第三种方法使用网络基础架构来实现ZTA。ZT可以通过使用overlay网络实现(即,第7层,但也可以设置在ISO网络堆栈的较低层)来实现。这些方法有时被称为软件定义边界(SDP)方法,通常包括来自SDN[SDNBOOK]和基于意图的网络(IBN)[IBNVN]的概念。在这种方法中,PA充当网络控制器,根据PE所做的决策建立和重新配置网络。客户端继续通过由PA组件管理的PEPs请求访问。】
【When the approach is implemented at the application network layer(i.e., layer 7), the most common deployment model is the agent/gateway (seeSection 3.2.1). In this implementation, the agent and resource gateway (acting as the single PEP and configured by the PA) establish a secure channel used for communication between the client and resource.】即【当该方法在应用网络层(即第7层)实现时,最常见的部署模型是代理/网关(见第3.2.1节)。在这种实现方法中,代理和资源网关(充当单个PEP并由PA配置)建立用于客户端和资源之间通信的安全通道。
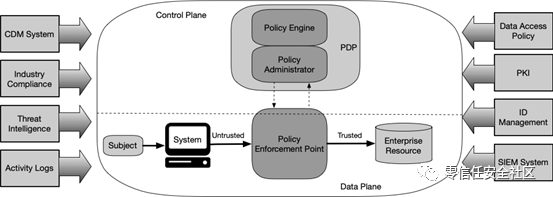
3.2 Deployed Variations of the Abstract Architecture
3.2.1 Device Agent/Gateway-Based Deployment
对于图3进行了修改,增加了subject方框。

(草案2中)设备代理/网关模型
3.2.2 Enclave-Based Deployment
题目从【基于微边界的部署】修改为【Enclave-Based Deployment】即【飞地部署】。
草案1中601行,【(e.g.,legacy database system that does not have an API that cannot be used to communicate with a gateway).】修改为【(e.g., legacy database system that does not have an application programming interface [API] that canbe used to communicate with a gateway).】即【(例如,传统数据库系没有不能用来与网关通信的API。)】修改为【例如,传统数据库没有可用于与网关通信的应用程序编程接口[API]。”】
草案1中图4,增加了subject方框,Gateway的部署位置作出了修正,和资源一样都在云端。

(草案2中)飞地部署模型
草案1中608行,【microperimeter gateways】,修改为【enclave gateways】,即【微边界网关】修改为【飞地网关】。
草案1中611行,【robust device management program】修改为【robust asset and configuration management program】即【稳健的设备管理程序】修改为【稳健的资产和配置管理计划】。
草案1中613行,删除【“Thisis a relaxation of the ZTA tenet that each resource should have its own PEPprotecting it.】
草案1中615行,“clients”修改为“subject”。
3.2.3 Resource Portal-Based Deployment
草案1中618行,【microperimeter】修改为【a secure enclave】即,【微边界】修改为【安全飞地】。
草案1中621行,图5增加主体,subject,enterprise system修改为system。
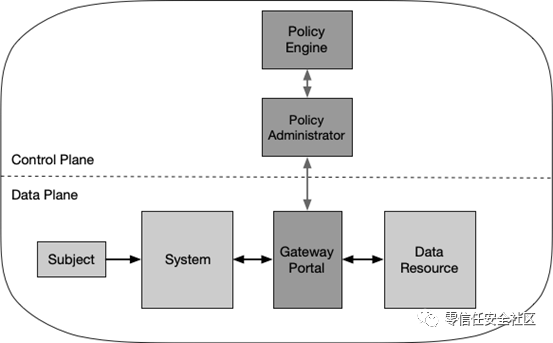
(草案2中)资源门户模型
草案1中624行【installed on all enterprise systems.】修改为【installed on all client devices.】即【安装在所有企业系统上】修改为【安装在所有客户端设备上。】
草案1中630行,删除【This model allows for more flexibility in client systems and BYOD policies and may make it easier to grant resource access to non-enterprise collaborators.】
草案1中634行,增加【The enterprise may be able to employ measures such as browser isolation to mitigate or compensate.】即【企业可以采取浏览器隔离等措施来缓解或补偿。】
草案1中636行,增加【The portal systems should be well-provisioned to provide availability against a DoS attackor network disruption.】即【门户系统应配置好,以提供抵御DoS攻击或网络中断的可用性。】
3.2.4 Device Application Sandboxing
题目从【System Application Sandboxing】(系统应用沙箱)修改为【Device Application Sandboxing】(设备应用沙箱)。
草案1中638行,【trusted applications】修改为【vetted applications or processes】即【可信应用】修改为【经审查的应用或进程】。
草案1中640行,【to protect the application from the host and other applications running on the system.】修改为【to protect the application or instances of applications from apossibly compromised host or other applications running on the asset.】即【以保护应用不受主机和系统上运行的其他应用的影响。】修改为【保护应用或应用实例不受可能受损的主机或资产上运行的其他应用的影响。】
草案1中645行,【trusted applications】修改为【approved, vetted applications】,即【可信应用】修改为【批准、审查的应用】。
草案1中653行,增加【The enterprise also needs to make sure each sandboxed application is secure, which may require more effort than simply monitoring devices.】即【企业还需要确保每个沙箱应用都是安全的,这可能需要比简单地监视设备需要花费更大精力。】
草案1中666行,【The actual request from the application.】修改为【This is the actual request from the subject.】即【来自应用的实际请求。】修改为【来自主体的实际请求】。
草案1中668行,【Depending onthe system state,】修改为【Depending on these factors and the asset security posture,】即【取决于系统状态】修改为【根据这些因素和资产安全姿态】。
草案1中671行,补充参考文献【SP800-63-3】。
草案1中671行,【enterprise】修改为【enterprise or collaborators】即【企业】修改为【企业或合作者】。
草案1中672行,【user attributes developed by the enterprise】修改为【user attributes/privileges assigned】即【企业开发的用户属性】修改为【已分配用户属性/权限】。
草案1中674行,【logical identity (e.g., account ID/password), biometric data (e.g., fingerprints,facial recognition, iris recognition, retina, and odor/scent), and behavior characteristics (e.g., typing rhythm, gait, and voice).】修改为【logical identity (e.g., account ID) and results of authentication checks performed by PEPs.】即【逻辑身份(如账户ID/密码)、生物测定数据(如指纹、面部识别、虹膜识别、视网膜和气味/味道)和行为特征(如打字节奏、步态和语音)。】修改为【逻辑身份(如账户标识)和PEP执行的认证检查结果。】
草案1中677行,【trust scores】修改为【confidence level】即【信任分】修改为【信任度】。
草案1中680行,增加【This may also include data about past observed user behavior in some (TA) variants (seeSection 3.3.1).】即【这也可能包括一些(TA,trustalgorithm,信任算法)变化中过去观察到的用户行为的数据(见第3.3.1节)】。
草案1中684行,删除“Trusted Platform Module (TPM)”。
草案1中685行,【Depending on the system state,】修改为【Depending on the asset state compared with this database】即【根据系统状态】修改为【根据资产状态与此数据库进行比较】。
草案1中688行,补充参考文献【SP800-63-3】。
草案1中691行,增加【data sensitivity (sometimes referred to as “data toxicity”)】即【数据敏感性(有时称之为“数据毒性”)】。
草案1中695行,【This can include attack signatures and mitigations.】修改为【These feeds can be external services or internal scans and discoveries and can include attack signatures and mitigations.】即【这可能包括攻击特征和缓解措施】修改为【这些feed可以是外部服务,也可以是内部扫描和发现,可以包括攻击签名和缓解措施。】
草案1中704行,增加【PAs may also place a hold or pause on a communication session to reauthenticate and reauthorize the connection in accordance with policy requirements.】即【PA还可以对通信会话进行保持或暂停,以便根据策略要求重新认证和重新授权连接。】
3.3 Trust Algorithm
3.3.1 Trust Algorithm Variations
草案1中710行,【either as binary decisions or weighted parts of a whole “score.”】修改为【whether as binary decisions or weighted parts of a whole “score” or confidence level.】即【要么是二元决策,要么是整个“分数”的加权部分】修改为【无论是二元决策,还是整体“得分”或信任度的加权部分】。
草案1中711行,【same user (or application) ID.】修改为【same subject, application, or device.】即【相同的用户(或应用)ID】修改为【相同的主体、应用或者设备】。
草案1中713行,【is granted to a resource.】修改为【is granted toa resource or an action (e.g., read/write) is allowed.】即【授予资源】修改为【授予资源或允许操作(例如读/写)】。
草案1中714行,【Access is granted to a resource 】修改为【Accessis granted or an action applied to a resource】即【授予对资源的访问权限】修改为【授予访问权限或对资源应用操作】。
草案1中715行,【A score-based TA computes a “score”】修改为【A score-based TA computes a confidence level】,即【基于分数的信任算法计算出一个分数】修改为【基于分数的信任算法计算出一个信任度】。
草案1中717行,【access is granted.】修改为【access is granted, orthe action is performed.】即【允许访问】修改为【授予访问权限,或执行操作。】
草案1中717行,【Otherwise, the access is denied.】修改为【Otherwise,the request is denied, or access privileges are reduced (e.g., read access is granted but not write access for a file).】即【否则,访问被拒绝。】修改为【否则,请求被拒绝,或访问权限降低(例如,授予读取权限,但不授予对文件的写入权限)。】
草案1中726行,【given user/agent.】修改为【given subject】,即【给定的用户/代理】修改为【给定的主体】。
草案1中726行,增加【Analysis of user behavior can be used to provide a model of acceptable use, and deviations from this behavior could trigger additional authentication checks or resource request denials.】即【用户行为分析可用于提供可接受使用的模型,与此行为的偏差可能会触发额外的身份认证检查或资源请求拒绝。】
草案1中727行,【trust score】修改为【confidence level】。
草案1中729行,【Likewise, a different TA may be score-based but be contextual in that every successful and failed access request could be used to change the ultimate trust score value.】修改为【However,contextual, score-based TAs work best, since the score provides a current confidence level for the requesting account.】即【同样,一个不同的TA可以是基于分数的,但必须是上下文的,因为每个成功和失败的访问请求都可以用来更改最终信任分数值。】修改为【但是,基于分数的、上下文的信任算法效果最好,因为分数为请求账户提供了当前的信任度。】
草案1中731行,【this may not always be possible】修改为【this may not always be possible with the infrastructure components available to the enterprise.】即【这并不总是行得通的】修改为【对于企业可用的基础设施组件,这并不总是行得通的。】
草案1中739行,增加【A contextual TA may also send an alert if someone is making access requests after normal business hours】即【如果有人在正常工作时间后提出访问请求,上下文可信算法也可能发送警报】。
草案1中751行,增加【How long this tuning phase lasts depends on the enterprise-defined metrics for progress and tolerance for incorrect access denials/approvals for the resources used in the workflow.】即【此优化阶段持续多长时间取决于企业定义的进度度量和对工作流中使用的资源的错误访问拒绝/批准的容忍度。】
3.4 Network/Environment Components
题目从【Network Components】(网络组件)修改为【Network/Environment Components】(网络/环境组件)。
草案1中758行,【infrastructure components】修改为【infrastructure components (both enterprise-owned and from service providers)】即【基础架构组件】修改为【基础架构组件(企业所有和服务提供商提供)】。
3.4.1 Network Requirements to Support ZTA
草案1中766行,【The local network】修改为【The local area network (LAN), enterprise controlled or not】即【局域网】限定为【局域网,无论是否由企业控制】。
草案1中769行,【The enterprise must be able to determine which systems are owned or managed by the enterprise and which devices are not owned or managed.】修改为【The enterprise must be able to distinguish between what assets areowned or managed by the enterprise and their current security posture.】即【企业必须能够确定哪些系统是企业拥有或管理的,哪些设备不是企业拥有或管理的。】修改为【企业必须能够区分企业拥有或管理的资产及其当前的安全姿态。】
草案1中771行,【MAC addresses,】修改为【network MAC addresses that can be spoofed).】即【MAC地址】修改为【可以伪造的网络MAC地址】。
草案1中774行,【but may not be able to perform Deep Packet Inspection (DPI) on all packets.】修改为【but may not be able to perform application layer inspection (i.e.,ISO layer 7) on all packets.】即【但可能无法对所有数据包执行深度数据包检查(DPI)】修改为【但可能无法对所有数据包执行应用层检查(即,ISO第7层)】。
草案1中776行,增加【to dynamically update policies and inform the PE in evaluating access requests.】即【在评估访问请求时动态更新策略并通知PE。】
草案1中777行,【discoverable】修改为【reachable】,即【可被发现】修改为【可被访问】。
草案1中780行,增加【Resources may not even be discoverable without accessing aPEP.】即【如果不访问PEP,资源甚至不可能被发现。】
草案1中781行,【This prevents attackers from scanning the network to identify targets and launching DoS attacks against resources.】修改为【This prevents attackers from identifying targets via scanning and launching DoS attacks against resources located behind PEPs.】即【这可防止攻击者扫描网络以识别目标并对资源发起DoS攻击。】修改为【这可防止攻击者通过扫描PEPs后面的资源并对其发起DoS攻击来识别目标。】
草案1中781行,增加【Note that not all resources should be hidden this way; some network infrastructure components (e.g., DNS servers) must be accessible.】即【请注意,并非所有资源都应以这种方式隐藏;某些网络基础结构组件(如DNS服务器)必须可访问】。
草案1中784行,【inaccessible】修改为【not directly accessible】,即【无法访问】修改为【无法直接访问】。
草案1中784行,【Enterprise systems use the data planewhen performing network tasks.】修改为【The data plane isused for application data traffic.】即【企业系统在执行网络任务时使用数据平面。】修改为【数据平面用于应用数据通信。】
草案1中789行,【access the PEP component on their enterprise ZTA network in order to gain access to resources.】修改为【access the PEP component to gain access to resources.】即【访问其企业ZTA网络上的PEP组件以获得对资源的访问】修改为【访问PEP组件以访问资源。】
草案1中790行,在web portal后补充一个【network device】。
草案1中792行,【The PEP is the only component that can access the Policy Administrator and Policy Engine.】修改为【The PEP is the only component that accesses the policy administrator as part of abusiness flow.】即【PEP是唯一可以访问PA和策略引擎的组件。】修改为【PEP是作为业务流的一部分访问PA的唯一组件。】
草案1中794行,【The PA may be discoverable, but only PEPs are allowed to connect.】修改为【All enterprise business process traffic passes through one or more PEPs.】即【PA是可以被发现的,但只有PEPs才允许连接。】修改为【所有企业业务流程流量都通过一个或多个PEP。】
草案1中801行,增加【The infrastructure used to support the ZTA access decision process should be made scalable to account for changes in process load. The PE(s),PA(s), and PEPs used in a ZTA become the key components in any business process. Delay or inability to reach a PEP (or inability of the PEPs to reach the PA/PE) negatively impacts the ability to perform the workflow. An enterprise implementing a ZTA needs to provision the components for the expected workload or be able to rapidly scale the infrastructure to handle increased usage when needed.】即【用于支持ZTA访问决策过程的基础架构应具有可扩展性,以考虑过程负载的变化。ZTA中使用的PE、PA和PEP成为任何业务流程中的关键组成部分。延迟或无法联系到PEP(或PEP无法联系到PA/PE)对执行工作流的能力产生负面影响。实现ZTA的企业需要为预期的工作负载提供组件,或者能够在需要时快速扩展基础设施以处理增加的使用量。】
草案1中802行,【For example, mobile systems may not be able to reach certain resources unless they are using enterprise network infrastructure.】修改为【For example, there may be a policy stating that mobile assets may not be able to reach certain resources if the requesting asset is located outside of the enterprise’s home country.】即【例如,移动系统可能无法访问到某些资源,除非它们使用企业网络基础设施。】修改为【例如,可能有一项策略规定,如果请求的资产位于企业之外,移动资产可能无法访问到某些资源】。
4 Deployment Scenarios/Use Cases
草案1中812行,【That said,any organization that has a sizable network with multiple resources can benefit from a zero trust architecture.】修改为【That said, any organizationcan benefit from a zero trust architecture.】即【也就是说,任何拥有具有多个资源的大型网络的组织都可以从零信任结构中获益。】修改为【也就是说,任何组织都可以从零信任结构中获益。】
4.1 Enterprise with Satellite Facilities
草案1中827行,【In this use case, the PE/PA is best hosted as a cloud service with end systems having a connection agent (see Section 3.1.1) or accessing a resource portal (see Section 3.1.3).】修改为【In this use case, the PE/PA(s) is often hosted as a cloud service(which usually provides superior availability and would not require remote workers to rely on enterprise infrastructure to access cloud resources) with end assets having an installed agent (see Section 3.2.1) or accessing a resource portal (see Section 3.2.3).】即【在这个用例中,PE/PA最好作为一个云服务托管,终端系统有一个连接代理(见第3.1.1节)或访问一个资源门户(见第3.1.3节)】修改为【在这个用例中,PE/PA通常作为云服务(通常提供更高的可用性,不需要远程工作者依赖企业基础设施来访问云资源)托管,终端资产具有已安装的代理(见第3.2.1节)或访问资源门户(见第3.2.3节)。】
草案1中830行,【in order to reach cloud services.】修改为【to reach applications hosted by cloud services.】即【为了达到云服务。】修改为【访问由云服务托管的应用。】
4.2 Multi-Cloud Enterprise
草案1中837行,【Sometimes,the application is hosted on a separate cloud service than the data source.】修改为【Sometimes, the application is hosted on a cloud service that is separate from the data source.】即【有时,应用托管在一个独立的云服务上,而不是数据源。】修改为【有时,应用托管在与数据源分离的云服务上。】
草案1中843行,删除“This multi-cloud use case is one of the main drivers of ZTA adoption. ”
草案1中848行,【infrastructure owned by any other service provider.】修改为【infrastructure owned and operated by any other service provider.】即【任何其他服务提供商拥有的基础设施。】修改为【任何其他服务提供商拥有和运营的基础设施。】
4.3 Enterprise with Contracted Services and/or Non-Employee Access
草案1中856行,【and employee work systems.】修改为【and assets.】将【员工工作系统】修改为【资产】。
草案1中867行,【They cannot even conduct network scans to look for enterprise services that may be visible (i.e.,prevent active network reconnaissance)】修改为【They may noteven be able to discover enterprise services via network scans (i.e., prevent active network reconnaissance/east-west movement).】即【他们甚至不能进行网络扫描以查找可能可见的企业服务(即,阻止主动网络侦察)】修改为【他们甚至可能无法通过网络扫描发现企业服务(即,阻止主动网络侦察/东西移动)。】
4.4 Collaboration Across Enterprise Boundaries
草案1中880行,增加【but this can quickly become difficult to manage. Having both organizations enrolled in a federated ID management system would allow quicke restablishment of these relationships provided that both organizations’ PEPs can authenticate subjects in a federated ID community.】即【但这很快就会变得难以管理。如果两个组织的PEP都可以在联合身份证社区中对主体进行身份认证,那么让两个组织都注册到联合身份证管理系统中可以更快地建立这些关系。】
草案1中888行,【Similar to use case 1, the PE and PA would ideally be hosted as a cloud service.】修改为【Similar to Use Case 1, a PE and PA hosted as a cloud service may provide availability to all parties without having to establish a VPN or similar.】即【与用例1类似,PE和PA在理想情况下将作为云服务托管。】修改为【与用例1类似,作为云服务托管的PE和PA可以向所有各方提供可用性,而无需建立VPN或类似的服务】。
4.5 Enterprise with Public- or Customer-Facing Services(新增)
新增一节4.5,标题为:面向公众或客户提供服务的企业。
【A common feature in many enterprises is a public-facing service that may or may not include user registration (i.e., users must create or have been issued a set of login credentials). Such services could be for the general public, a set of customers with an existing business relationship, or a special set of nonenterprise users such as employee dependents. In all cases, it is likely that requesting assets are notenterprise-owned, and the enterprise is constrained as to what internal cybersecurity polices can be enforced. For a general, public-facing resource that does not require login credentials to access (e.g., public web page), the tenets of ZTA do not directly apply. The enterprise cannot strictly control the state of requesting assets, and public resources do not require credentials in order to be accessed. Enterprises may establish policies for registered public users such as customers (i.e., those with a business relationship) and special users(e.g., employee dependents). If the users are required to produce or are issued credentials, the enterprise may institute policies regarding password length, lifecycle, and other details and may provide MFA as an option or requirement.However, enterprises are limited in the policies they can implement for this class of user. Information about incoming requests may be useful in determining the state of the public service and detecting possible attacks masquerading as legitimate users. For example, a registered user portal is known to be accessedby registered customers using one of a set of common web browsers. A sudden increase in access requests from unknown browser types or known outdated versions could indicate an automated attack of some kind, and the enterprise could take steps to limit requests from these identified clients. The enterprise should also be aware of any statutes or regulations regarding what information can be collected and recorded about the requesting users and assets.】即【许多企业的一个共同特点是面向公众的服务,可能包括也可能不包括用户注册(即,用户必须创建或已获得一组登录凭据)。这类服务可以面向公众、一组与现有业务关系的客户,或者一组特殊的非企业用户(如员工家属)。在所有情况下,请求的资产很可能不是企业所有的,并且企业在哪些内部网络安全策略可以实施方面受到限制。对于不需要登录凭据才能访问的一般面向公共的资源(例如,公共网页),ZTA的原则并不直接适用。企业无法严格控制请求资产的状态,公共资源不需要凭据才能访问。企业可以为注册公共用户(如客户(即与企业有业务关系的用户)和特殊用户(如员工家属)制定策略。如果要求用户出示或获得颁发的凭据,企业可以制定有关密码长度、生命周期和其他详细信息的策略,并可以提供MFA作为选项或要求。然而,企业在为这类用户实现策略方面受到限制。有关传入请求的信息可能有助于确定公共服务的状态并检测伪装为合法用户的可能攻击。例如,已知注册用户门户由注册客户使用一组通用web浏览器中的一个访问。来自未知浏览器类型或已知过时版本的访问请求突然增加可能表示某种自动攻击,企业可以采取措施限制来自这些已标识客户端的请求。企业还应了解有关可收集和记录请求用户和资产的哪些信息的任何法规或条例。】
5 Threats Associated with Zero Trust Architecture
草案1中896行,【However,there are some threat risks unique to ZTA.】修改为【However,some threats have unique features when implementing a ZTA.】即【不过,ZTA有其特有的威胁风险】修改为【然而,在实施ZTA时,面临一些特有的威胁】。
5.2 Denial-of-Service or Network Disruption
草案1中910行,【(i.e.,denial-of-service (DoS) attack)】修改为【(i.e., DoS attack or route hijack)】即增加【路由劫持】。
草案1中920行,【There is also the possibility of the hosting provider accidently taking the Policy Administrator offline. Similar to the Amazon S3 outage in February 20174 that prevented access to customers,…】修改为【A hosting provider may also accidentally take a cloud-based PE or PA offline. Cloud services have experienced disruptions in the past, both infrastructure as a service andSaaS.】即【托管提供商也可能意外地使PA下线。类似于1974年2月亚马逊S3的中断,它阻止了用户的访问,】修改【托管提供商也可能意外地使基于云的PE或PA离线。云服务在过去经历过中断,包括IaaS和SaaS。】
草案1中925行,增加一句【This could happen due to an attack or simply due to unexpected heavy usage.】即【这可能是由于攻击或只是由于意外的大量使用】。
5.3 Stolen Credentials/Insider Threat
5.3题目从【Insider Threat】(内部威胁)修改为【Stolen Credentials/Insider Threat】(被盗凭据/内部威胁)。
草案1中930行,【reduce the risk of an insider attack.】修改为【reduce the risk of an attacker gaining broad access via stolen credentials or insider attack. The ZT principle of no implicit trust based on network location means attackers need to compromise an existing account or device to gain a foothold in an enterprise.】即【降低内部攻击的风险】修改【降低攻击者通过被盗凭据或内部攻击获得广泛访问权限的风险。ZT基于网络位置的无隐式信任原则意味着攻击者只能靠破坏某个已有帐户或设备才能在企业中站住脚。】
草案1中932行,增加【This means that accounts with access policies around resources that an attacker is interested in would be the primary targets for attackers.】即【这意味着针对攻击者感兴趣的资源具有访问策略的帐户将成为攻击者的主要目标。】
草案1中932行,【Implementation of MFA for network access may also reduce the risk of access from a compromised account. However, just like traditional enterprises, an attacker with valid credentials (or a malicious insider) may still be able to access resources for which the account has been granted access. For example, an attacker (or compromised employee) who has the credentials and enterprise-owned system of a valid human resources employee may still be able to access an employee database.】修改【Attackers may use phishing, social engineering, or a combination of attacks to obtain credentials of valuable accounts. “Valuable” may mean different things based on the attacker’s motivation. For instance, enterprise administrator accounts may be valuable, but attackers interested in financial gain may consider accounts that have access to financial or payment resources of equal value. Implementation of MFA for network access may reduce the risk ofaccess from a compromised account. However, just like traditional enterprises,an attacker with valid credentials (or a malicious insider) may still be able to access resources for which the account has been granted access. For example,an attacker or compromised employee who has the credentials and enterprise-owned asset of a valid human resources employee may still be able to access an employee database.】即【为网络访问实施MFA还可以降低从受损帐户访问的风险。但是,与传统企业一样,具有有效凭据的攻击者(或恶意内部人员)可能仍然能够访问已授予帐户访问权限的资源。例如,具有有效人力资源员工的凭据和企业拥有的系统的攻击者(或受攻击的员工)仍然可以访问员工数据库。】修改为【攻击者可以使用网络钓鱼、社会工程或攻击组合来获取有价值帐户的凭据。基于攻击者的动机,“有价值”可能意味着不同的事情。例如,企业管理员帐户可能是有价值的,但对财务收益感兴趣的攻击者可能会考虑访问同等价值的财务或支付资源的帐户。为网络访问实施MFA可以降低从受损帐户访问的风险。但是,与传统企业一样,具有有效凭据的攻击者(或恶意内部人员)可能仍然能够访问已授予帐户访问权限的资源。例如,具有有效人力资源员工的凭据和企业拥有的资产的攻击者或受损员工可能仍然能够访问员工数据库。】
草案1中939行,增加一句【If the compromised credentials are not authorized to access a particular resource,they will continue to be denied access to that resource.】即【如果遭破坏的凭据未被授权访问特定资源,则它们将继续被拒绝访问该资源。】
草案1中946行,【may be opaque to network analysis tools.】修改为【may be opaque to traditional layer 3 network analysis tools.】即【可能对网络分析工具不透明】修改为【可能对传统的第3层网络分析工具不透明】。
5.5 Storage of Network Information
草案1中961行,【are being stored for further analysis,】修改为【are being stored for building contextual policies, forensics, or later analysis,】即【正在存储以供进一步分析,】修改为【存储用于构建上下文策略、取证或后期分析】。
草案1中966行,【network】修改为【enterprise】。
草案1中972行,【from designated (or dedicated) administrator accounts.】修改为【only from designated or dedicated administrator accounts】即,【来自指定(或专用)管理员帐户】修改为【仅来自指定或专用管理员帐户】。
5.7 Use of Non-Person Entities(NPE) in ZTA Administration
草案1中994行后,增加【The biggest risk when using automated technology for configuration and policy enforcement is the possibility of false positives (innocuous actions mistaken for attacks) and false negatives (attacks mistaken for normal activity). This can be reduced with regular retuning analysis to correct mistaken decisions and improve the decision process.】即【在使用自动化技术进行配置和策略实施时,最大的风险是可能出现假阳性误报(无害操作被误认为是攻击)和假阴性误报(攻击被误认为是正常活动)。这可以通过定期的重新调整分析来减少,以纠正错误的决策并改进决策过程。】
6 Zero Trust Architecture and Possible Interactions with Existing Federal Guidance
题目从【Zero Trust Architecture and Existing Federal Guidance】(零信任架构与现有联邦指南)修改为【Zero Trust Architecture and Possible Interactions with Existing Federal Guidance】(零信任架构与现有联邦指南的可能关联)。
6.1 ZTA and NIST Risk Management Framework
草案1中1014行,【but this is disproportionately restrictive in most cases.】修改为【but this is disproportionately restrictive in the majority of cases and inhibits work from being accomplished.】即,【但在大多数情况下,这是过度限制。】修改为【但在大多数情况下,这一点限制性太大,阻碍了工作的完成。】
6.2 ZTA and NIST Privacy Framework
草案1中1026行,增加参考文献[NISTPRIV]。
草案1中1028行,增加【This includes personal information used by the enterprise to support ZTA operations and any biometric attributes used in access request evaluations.】即【这包括企业用于支持ZTA操作的个人信息以及访问请求评估中使用的任何生物特征属性。】
草案1中1029行,【Part of the core requirements for ZTA is that an enterprise should inspect and log all traffic on its network. This includes decrypting traffic as much as possible to enable inspection.】修改为【Part of the core requirements for ZTA is that an enterprise should inspect and log traffic (or metadata when dealing with encrypted traffic) in its environment.】即,【ZTA的核心要求之一是,企业应检查并记录其网络上的所有流量。这包括尽可能对通信量进行解密以启用检查。】修改为【ZTA的核心要求之一是,企业应该检查并记录其环境中的流量(或处理加密流量时的元数据)。】
草案1中1033行,补充参考文献,[NISTIR8062]。
6.6 ZTA and Continuing Diagnosticsand Mitigations (CDM)
草案1中1093行,【to improve federal agency IT security posture.】修改为【to improve federal agency information technology (IT).】即【改善联邦机构IT安全姿态】修改为【改进联邦机构信息技术(IT)。】
草案1中1106行,【at rest and in transit】修改为【at rest, in transit, and in use.】
草案1中1108行,【an enterprise must have a complete inventory of both physical and virtual assets.】修改为【an enterprise must have a system to discover and record physical andvirtual assets to create a usable inventory.】即【企业必须有完整的物理和虚拟资产库存。】修改为【企业必须有一个系统来发现和记录物理和虚拟资产,以创建可用的库存。】
草案1中1114行,【network】修改为【network (or those accessing resources remotely)】即【网络(或远程访问资源的网络)】。
6.7 ZTA, Cloud Smart, and the Federal Data Strategy
草案1中1123行,【since the users and resources are located outside of the enterprise network perimeter.】修改为【because the users and resources are located outside of the enterprise network perimeter and are likely to see the most benefit in use,scalability, and security】即【由于用户和资源位于企业网络边界之外。】修改为【因为用户和资源位于企业网络边界之外,他们最能体会到在易用性、可扩展性和安全性方面的益处。】
7 Migrating to a Zero Trust Architecture
7.1 Pure Zero Trust Architecture
草案1中1146行,【it is an engineering exercise】修改为【it is an engineering and organizational exercise in】即【这是一项工程练习】修改为【这是一项工程和组织工作】。
草案1中1147行,增加【This may include additional organizational changes depending on how the enterprise is currently set up and operating.】即【这可能会带来额外的组织变更,具体取决于企业当前的设置和运行方式。】
7.3 Steps to Introducing ZTA to a Legacy Architected Network
草案1中1167行,【users】修改为【users (including user privileges)】即【用户】修改为【用户(包括用户权限)】。
草案1中1169行,增加【This is especially an issue if there are unknown “shadow IT” deployments operating within an organization.】即【如果组织中有未知的“影子IT”部署在运行,就明显会成为一个问题。】。
草案1中1171行,【users】后面补充【data flows, and workflows.】,补充【数据流和工作流】。
草案1中1176行,图12修改1)增加了准备阶段;2)RMP steps增加了反馈箭头(策略的扩展);3)下面增加了feedback。

(草案2中)ZTA 部署周期
7.3.1 Identify Actors on the Enterprise
草案1中1187行,【need additional consideration】修改为【require additional scrutiny】即【需要额外考虑】修改为【要求额外的检查】。
草案1中1191行,【while logging and auditing behavior.】修改为【while using logs andaudit actions to identify access behavior patterns.】即【同时记录和审核行为】修改为【同时使用日志和审核操作来标识访问行为模式。】
7.3.2 Identify Assets Owned by the Enterprise
草案1中1195行,【the ability to identify and manage enterprise-owned devices.】修改为【the ability to identify and manage devices.】即【识别和管理企业拥有的设备的能力。】修改为【识别和管理设备的能力。】
草案1中1199行,增加【It may not be possible to conduct a complete census on all enterprise-owned assets, so an enterprise should consider building the capability to quickly identify, categorize, and assess newly discovered assets that are on enterprise-owned infrastructure.】即【可能无法对所有企业拥有的资产进行全面的普查,因此企业应考虑建立快速识别、分类和评估企业拥有的基础设施上新发现的资产的能力。】
草案1中1207行,【Non-enterprise-ownedassets should also be cataloged to the best extent possible.】修改为【Non-enterprise-owned assets and enterprise-owned “shadow IT” should also be cataloged as well as possible.】即【非企业所有的资产也应尽可能地分类。】修改为【非企业所有资产和企业所有的“影子IT”也应尽可能分类。】
草案1中1201行,【for monitoring by the enterprise.】修改为【for monitoring and forensics logging by the enterprise.】即【即企业监控】修改为【用于企业监视和取证日志记录】。
草案1中1201行,增加【Shadow IT presents a special problem in that these resources are enterprise-owned but not managed like other resources. Certain ZTA approaches (mainly network-based) may even cause shadow IT components to become unusable as they may not be known and included in network access policies.】即【影子它提出了一个特殊的问题,因为这些资源是企业拥有的,而不是像其他资源一样管理。某些ZTA方法(主要是基于网络的方法)甚至可能导致影子IT组件变得不可用,因为它们可能不知道并包含在网络访问策略中。】
7.3.3 Identify Key Processes and Evaluate Risks Associated with Executing Process
草案1中1221行,【rank the business processes (i.e., missions) of the agency.】修改为【rank the business processes, data flows, and their relation in the missions of the agency.】即【“对机构的业务流程(即任务)进行排序。】修改为【对机构任务中的业务流程、数据流及其关系进行排序。】
草案1中1228行,增加【and would likely see improvements to availability and security.】即【而且可能会看到易用性和安全性的改善】。
草案1中1228行,删除【This is because the clients and resources are outside of the enterprise perimeter,one of the main advantages of ZTA over legacy enterprise network architecture.”】
7.3.4 Formulating Policies for the ZTA Candidate
草案1中1240行,【the next step is to identify the user set that would be affected. ”修改为“identify all upstream resources (e.g., ID management systems, databases, micro-services), downstream resources (e.g., logging, security monitoring), and entities (e.g., users, service accounts) that are used or affected by the workflow.】即【下一步是确定将受影响的用户集】修改为【确定使用或受工作流影响的所有上游资源(如ID管理系统、数据库、微服务)、下游资源(如日志记录、安全监控)和实体(如用户、服务帐户)。】
7.3.5 Identifying Candidate Solutions
草案1中1262行,增加【Does the solution provide a means to log interactions for analysis?A key component of ZT is the collection and use of data related to the process flow that feeds back into the PE when making access decisions.】即【该解决方案是否提供了记录交互以进行分析的方法?ZT的一个关键组成部分是收集和使用与在做出访问决策时反馈到PE的过程流相关的数据。】
7.3.6 Initial Deployment and Monitoring
草案1中1270行,【may wish to make them more lenient at first.】修改为【may wish to operate in an observation and monitoring mode at first. 】即【一开始不妨让它们更宽松些。】修改为【可能希望首先以观察和监视模式进行操作。】
7.3.7 Expanding the ZTA
草案1中1282行,【After enough confidence is gained in the workflow policy set】修改为【When enough confidence is gained and the workflow policy set is refined】即【在对工作流策略集获得足够的信任之后】修改为【当获得足够的信任并细化工作流策略集时】。
草案1中1285行,增加【The users and stakeholders of the resources and processes involved should also provide feedback to improve operations.】即【相关资源和流程的用户和利益相关者也应提供反馈,以改进运营。】
增加的参考文献:
[BCORE] 、[FIPS199]、[IBNVN]、[NISTIR 8062]、[NISTPRIV]、[SDNBOOK]、[SP800-63-3]
声明:本文来自零信任安全社区,版权归作者所有。文章内容仅代表作者独立观点,不代表安全内参立场,转载目的在于传递更多信息。如有侵权,请联系 anquanneican@163.com。
