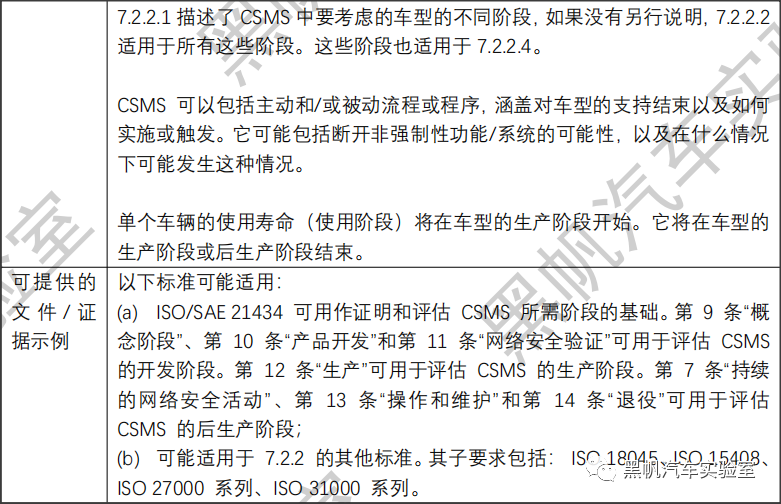
本文翻译自世界车辆法规协调论坛(WP.29)自动驾驶/自动驾驶和联网车辆工作组(GRVA)的解释文档。该文对UN R155 CSMS审核的目的、依据和细节做了较充分的逐条阐述。本篇聚焦于法规7.2节——CSMS的要求,希望对读者深入理解CSMS审核和申请工作有所帮助。











附UN R155相关原文:
7.2 Requirements for the Cyber Security Management System
7.2.1
For the assessment the Approval Authority or its Technical Service shall verify that the vehicle manufacturer has a Cyber Security Management System in place and shall verify its compliance with this Regulation.
7.2.2
The Cyber Security Management System shall cover the following aspects:
7.2.2.1
The vehicle manufacturer shall demonstrate to an Approval Authority or Technical Service that their Cyber Security Management System applies to the following phases:
(a) Development phase;
(b) Production phase;
(c) Post-production phase.
7.2.2.2
The vehicle manufacturer shall demonstrate that the processes used within their Cyber Security Management System ensure security is adequately considered, including risks and mitigations listed in Annex 5. This shall include:
(a) The processes used within the manufacturer’s organization to manage cyber security;
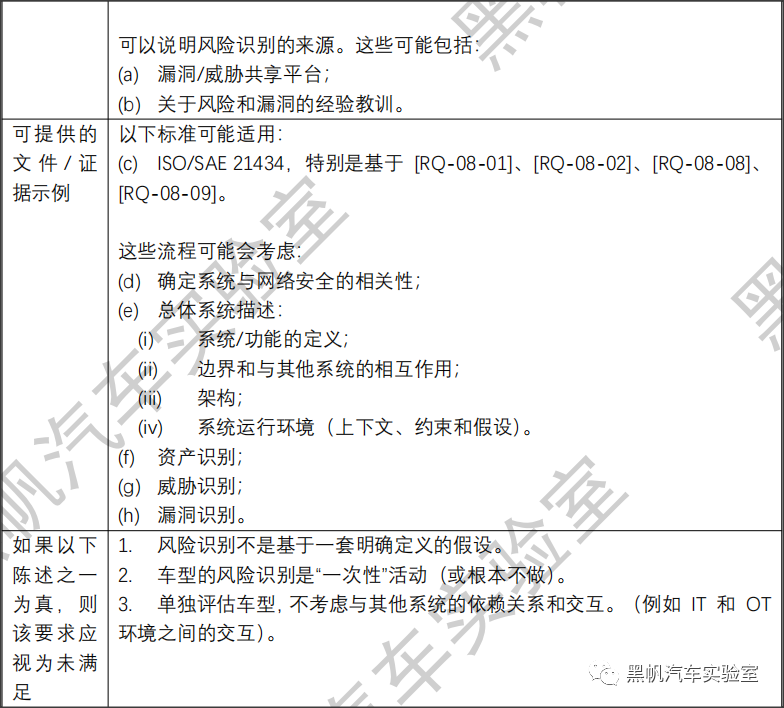
(b) The processes used for the identification of risks to vehicle types. Within these processes, the threats in Annex 5, Part A, and other relevant threats shall be considered;
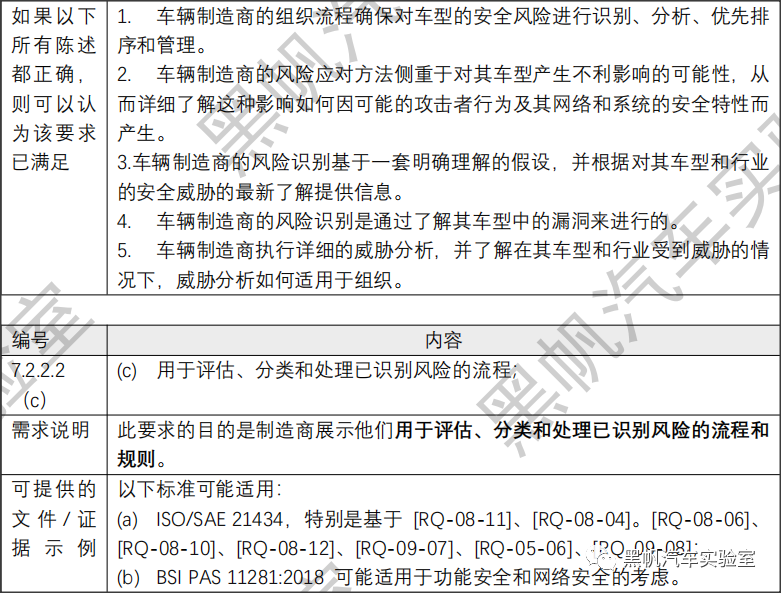
(c) The processes used for the assessment, categorization and treatment of the risks identified;
(d) The processes in place to verify that the risks identified are appropriately managed;
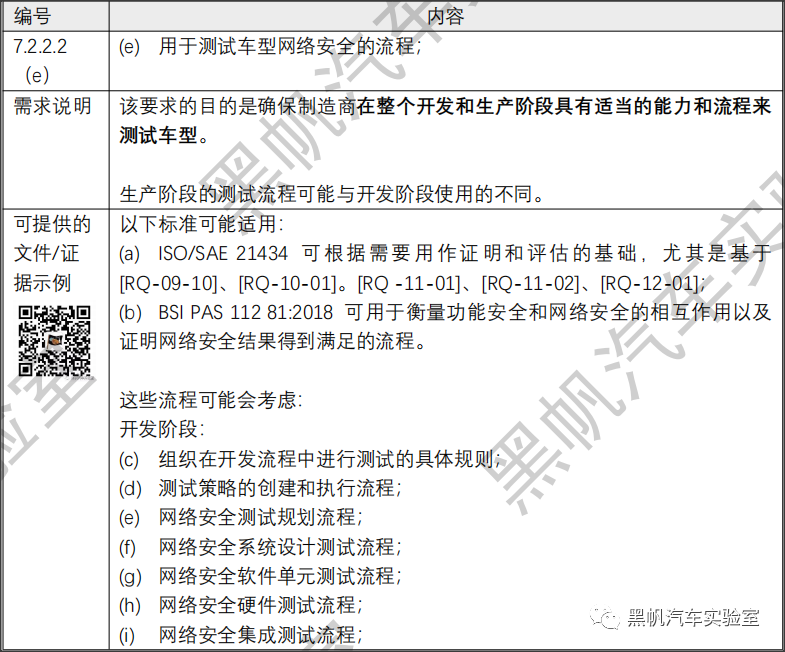
(e) The processes used for testing the cyber security of a vehicle type;
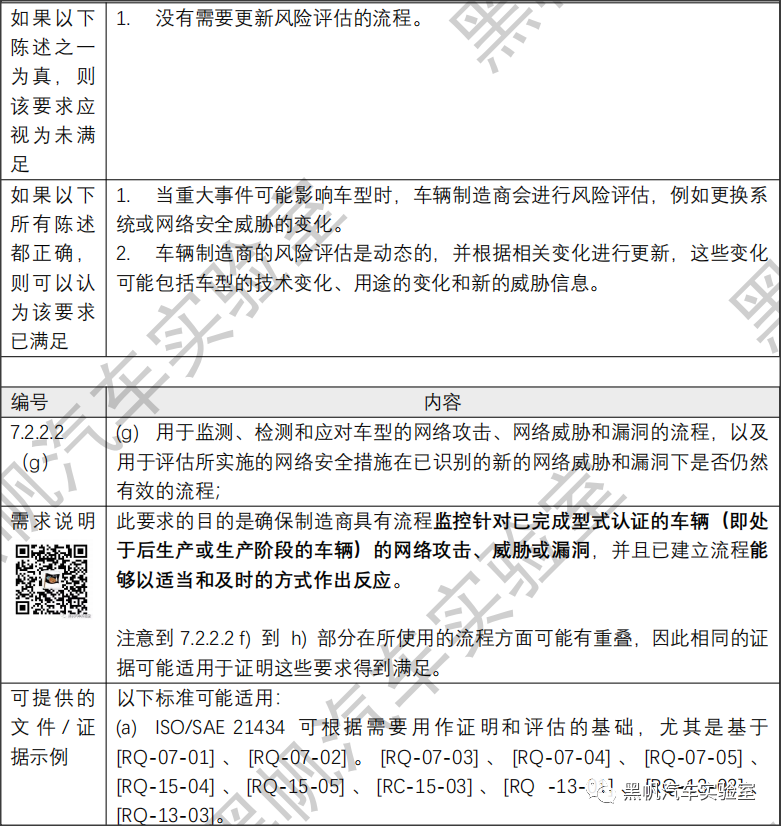
(f) The processes used for ensuring that the risk assessment is kept current;
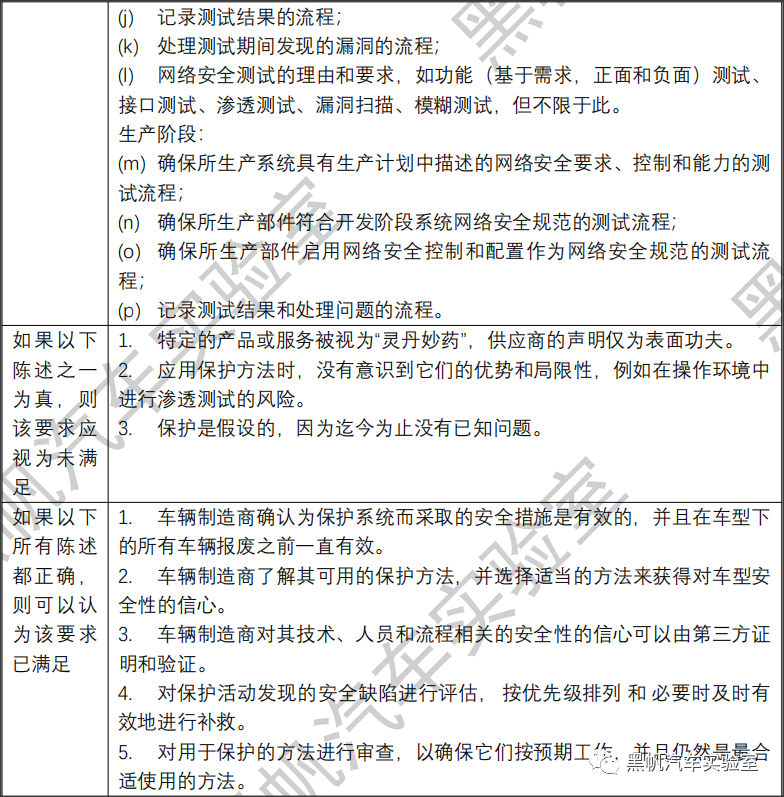
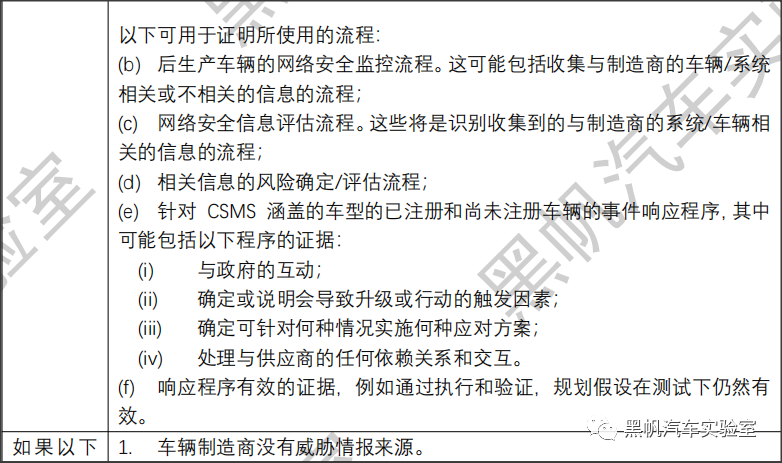
(g) The processes used to monitor for, detect and respond to cyber-attacks, cyber threats and vulnerabilities on vehicle types and the processes used to assess whether the cyber security measures implemented are still effective in the light of new cyber threats and vulnerabilities that have been identified.
(h) The processes used to provide relevant data to support analysis of attempted or successful cyber-attacks.
7.2.2.3
The vehicle manufacturer shall demonstrate that the processes used within their Cyber Security Management System will ensure that, based on categorization referred to in paragraph 7.2.2.2 (c) and 7.2.2.2 (g), cyber threats and vulnerabilities which require a response from the vehicle manufacturer shall be mitigated within a reasonable timeframe.
7.2.2.4
The vehicle manufacturer shall demonstrate that the processes used within their Cyber Security Management System will ensure that the monitoring referred to in paragraph 7.2.2.2 (g) shall be continual. This shall:
(a) Include vehicles after first registration in the monitoring;
(b) Include the capability to analyse and detect cyber threats, vulnerabilities and cyber-attacks from vehicle data and vehicle logs. This capability shall respect paragraph 1.3. and the privacy rights of car owners or drivers, particularly with respect to consent.
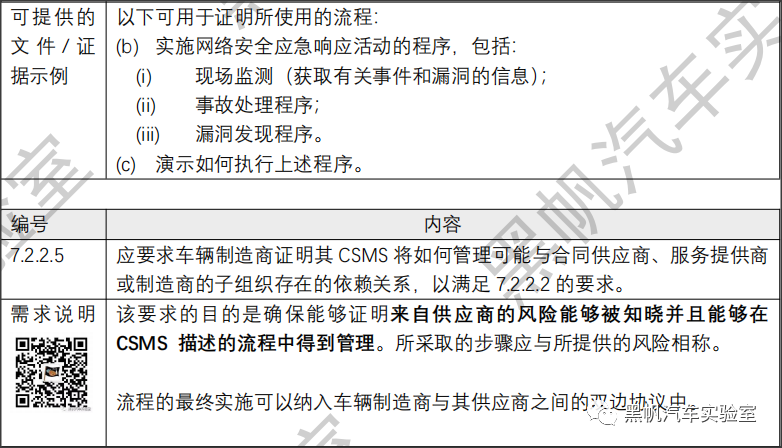
7.2.2.5
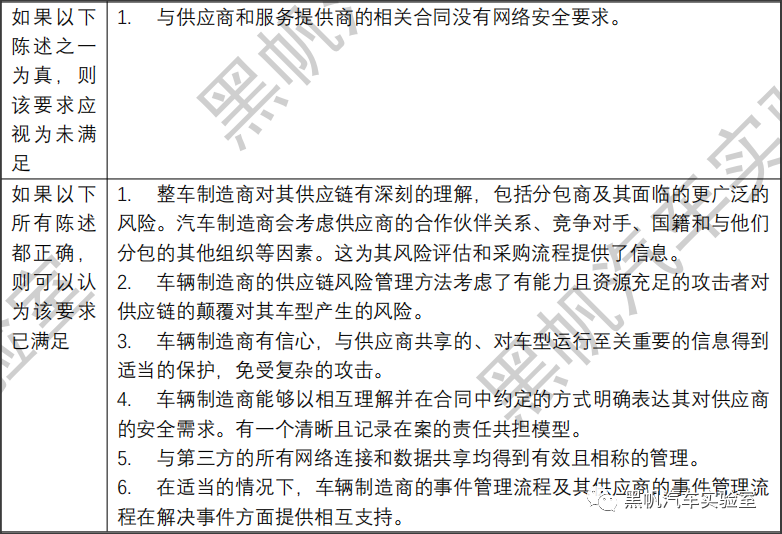
The vehicle manufacturer shall be required to demonstrate how their Cyber Security Management System will manage dependencies that may exist with contracted suppliers, service providers or manufacturer’s sub-organizations in regards of the requirements of paragraph 7.2.2.2.
声明:本文来自黑帆汽车实验室,版权归作者所有。文章内容仅代表作者独立观点,不代表安全内参立场,转载目的在于传递更多信息。如有侵权,请联系 anquanneican@163.com。
