安全圈最著名的“网友见面会”——RSAC2019,今天在美国旧金山开幕,本次大会的演讲PPT已经提前披露,有大量热点话题:
· 如何破解生物识别技术?
· 如何黑进人类的大脑?
· 卫星真的会收到攻击吗?
· 航空业与物联网安全漫谈…
· 黑进多因素认证系统的12种方法…
· CloudNative火爆,如何保障云原生应用的安全?
· 在K8S的运行环境下,有哪些安全的坑?
· 人人都谈DevOps,如何实现DevSecOps?
· 从4G演进到5G,有哪些新的安全问题?
· 如何量化数据泄露带来的损失?
· 量子计算机安全吗?
· 如果代码都是机器写出来的,那么你的应用系统安全吗?
· ServerLess架构下的安全攻防
……
是不是干货超多?噱头十足?
为了让大家更好的围观这次大会,我们将PPT进行了初步的整理。
公众号后台回复“rsa2019”,获取全套221个PPT。
以下为部分热门PPT掠影
专题一丨云安全与虚拟化Cloud Security & Virtualization
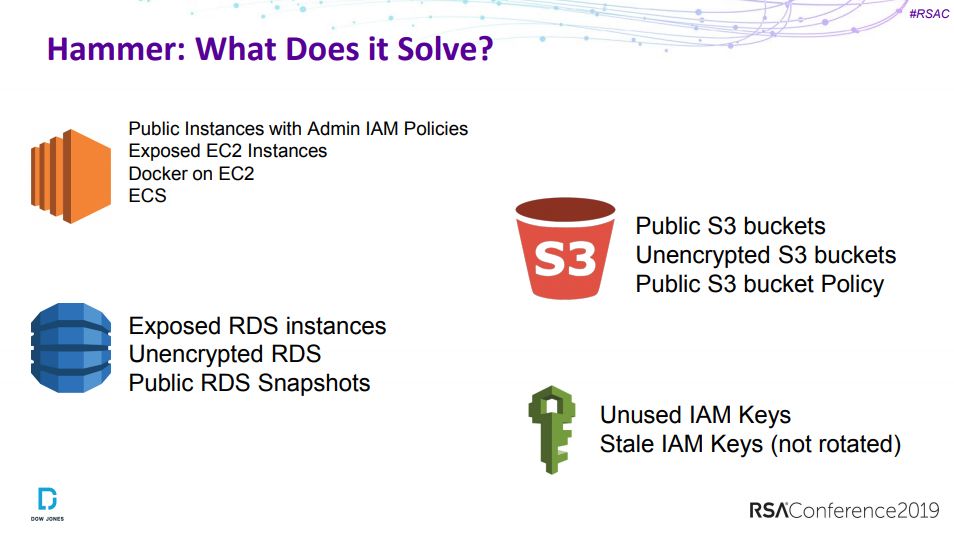
1、公有云安全之旅
Democratizing Cloud Security: Journey to Secure the Public Cloud

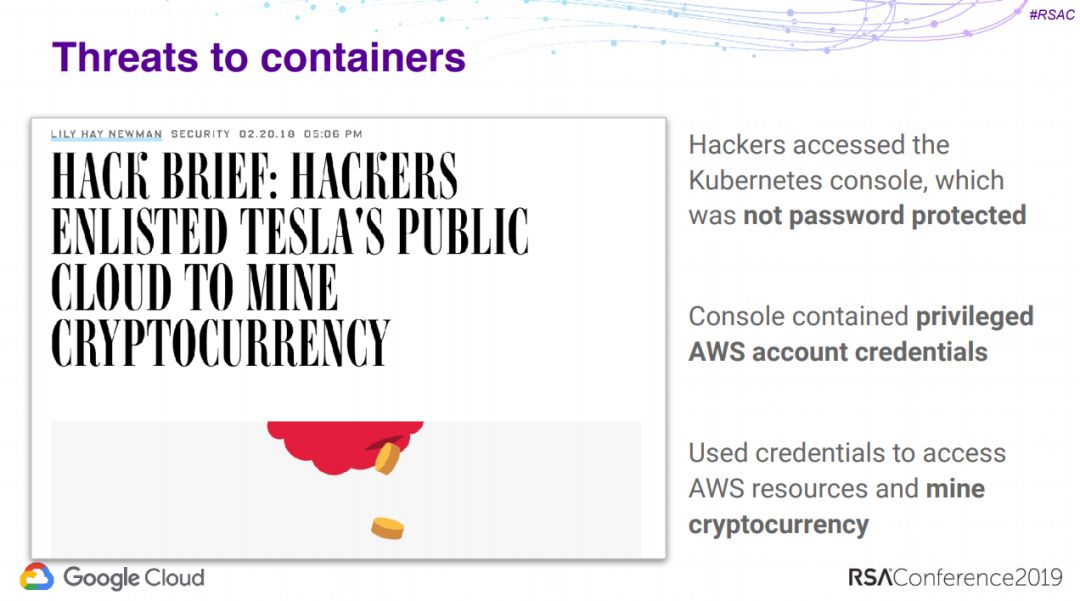
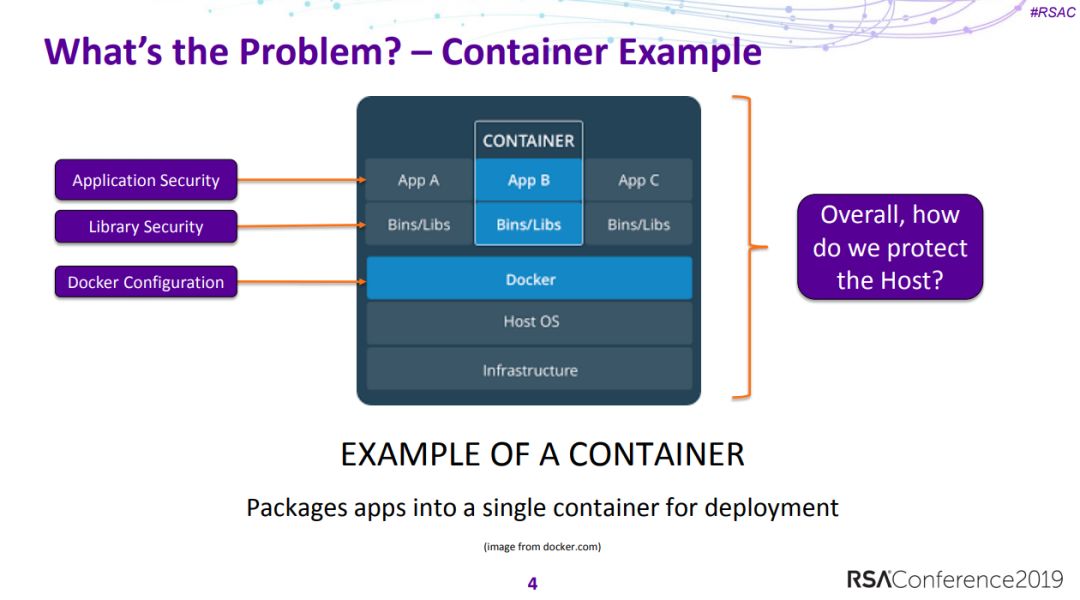
2、K8S运行安全:如果一个容器变坏会怎样?
Kubernetes Runtime Security: What Happens if a Container Goes Bad?
3、用云的力量来保护云
Protecting the Cloud with the Power of Cloud
4、红军视角:无服务器架构下的攻防
Red Team View: Gaps in the Serverless Application Attack Surface

5、公有云中的安全创新,神话还是现实?
Secure Innovation in Public Cloud, Myth or Reality?

6、如何安全的部署微服务、容器、Serverless应用
Securely Deploying Micro Services, Containers and Serverless PaaS Web Apps

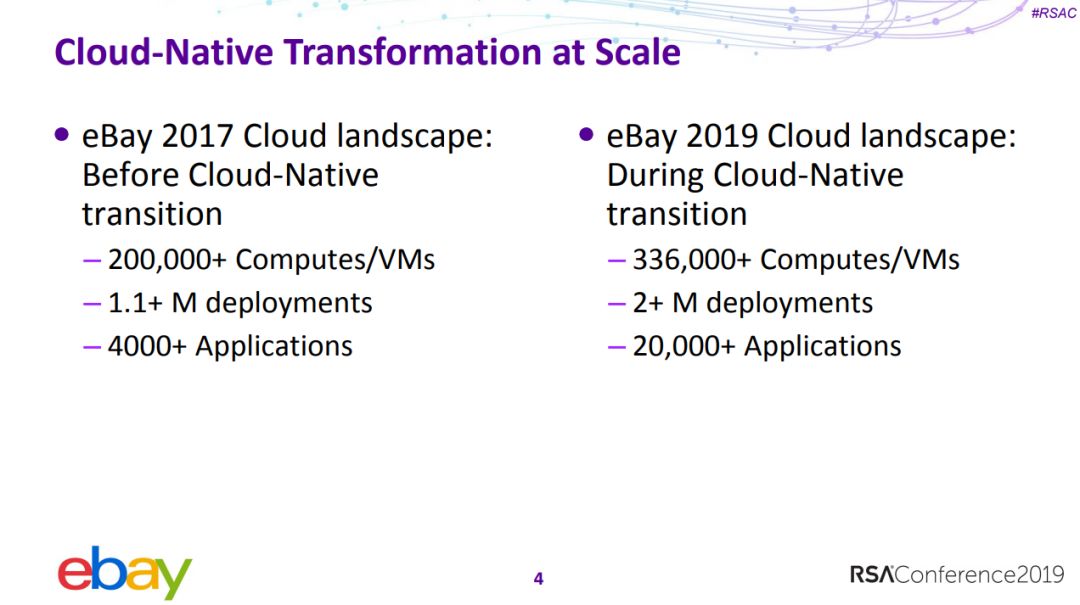
7、如何保障规模化云原生应用的安全
Securing Cloud-Native Applications at Scale
8、DevOps实时安全检测
Security at the Speed of DevOps: A Reality Check

9、基于自动修复来响应云上安全威胁
Treating Cloud-Specific Threats with Automatic Remediation

专题二丨智能分析与响应Analytics Intelligence &Response
1、ATTACK in Practice: A Primer to Improve Your Cyber-Defense

2、How CTI Can Play a Key Role to Get Security on Board
3、Incident Response beyond Enterprise IT

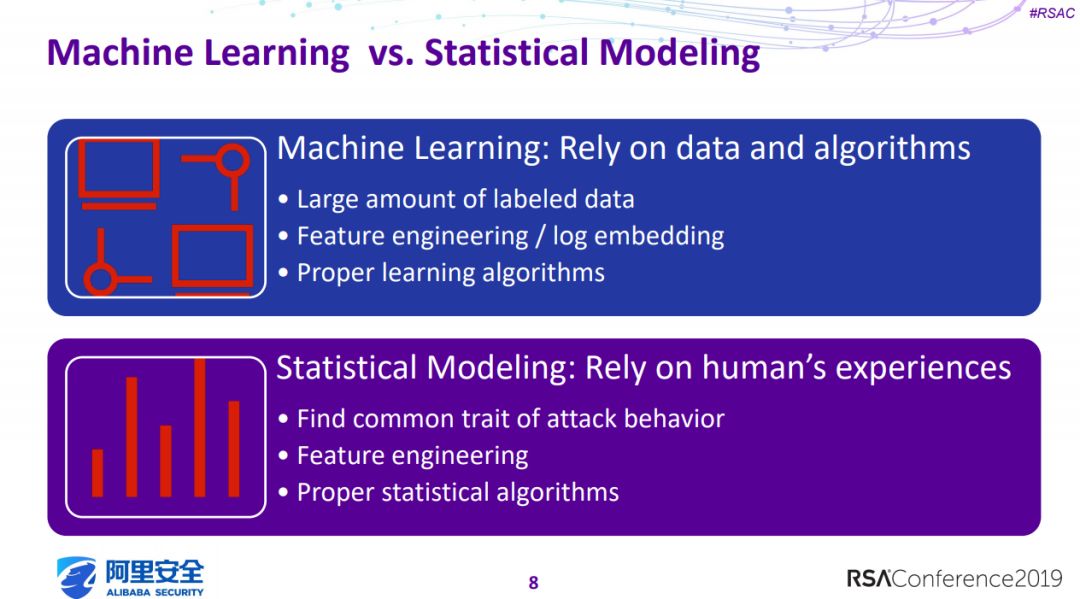
4、Use Model to Deconstruct Threats: Detect Intrusion by Statistical Learning
专题三丨应用安全与DevSecOpsApplication Security & DevSecOps
1、Container Security at the Speed of CI/CD
2、DevSecOps for the Rest of Us!
3、云原生安全实践
Practical Approaches to Cloud Native Security

4、2019威胁模型
Threat Modeling in 2019
5、如果代码都是机器生产的,那么你的应用系统安全吗?
Will Your Application Be Secure Enough When Robots Produce Code for You?
专题四丨区块链与加密应用Blockchain&Applied Crypto
1、Automated Fault Analysis of Block Cipher Implementations
2、Blockchainification of Cyber-Supply Chain Risk: Hype vs. Hope

3、Cryptojacking: What’s in Your Environment?

4、揭开量子计算机的神秘面纱
Demystifying Quantum Computers

5、How Bad Incentives Led to Crypto-Mining Malware, and What to Do about It
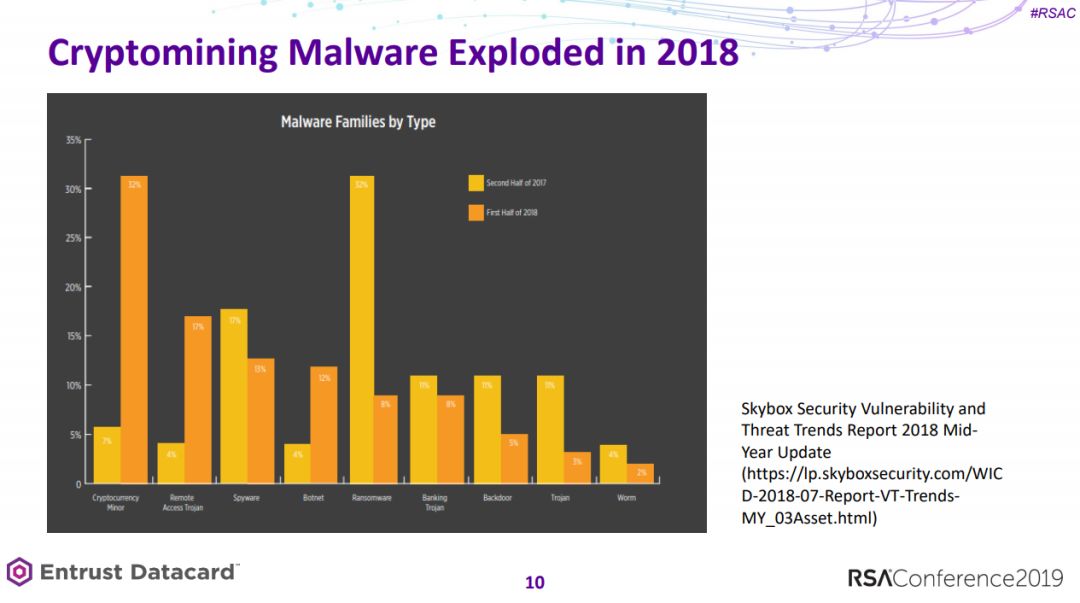
6、Mechanical Backdoors in Cold War Encryption Machines

7、Using High-Entropy Encryption for Enterprise Collaboration

专题五丨风险治理与合规
Governance Risk&Compliance
1、数据泄露:一份定量风险分析
Data Breach or Disclosure: A Quantitative Risk Analysis
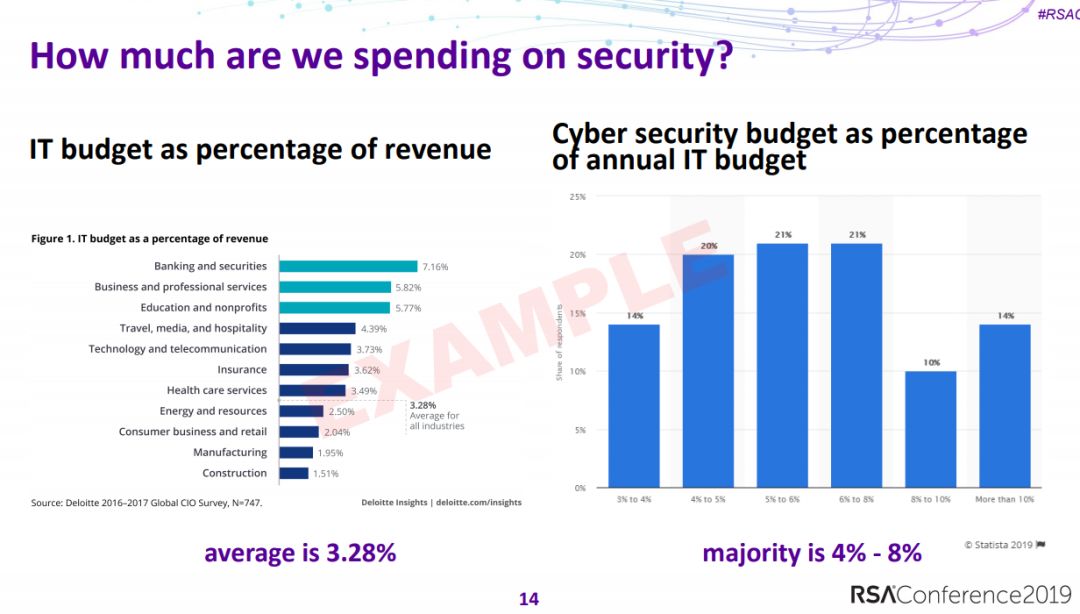
2、如何知道组织的10大安全风险
Do You Know Your Organization’s Top 10 Security Risks?

3、Finding the Right Answers—Facilitating Insider Threat Analysis Using OCTAVE
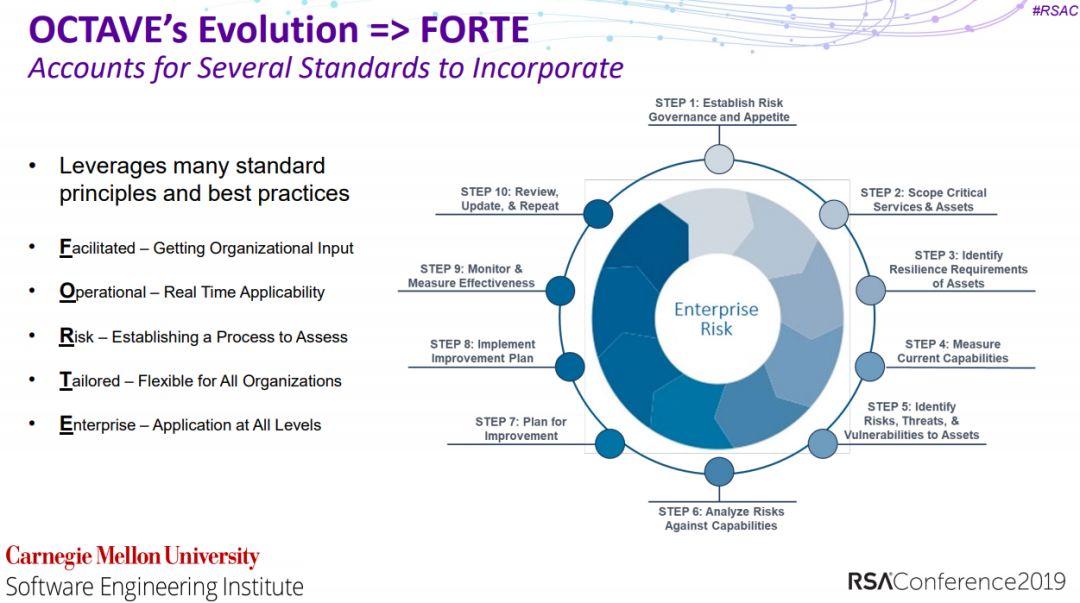
4、GDPR: How to Work Out If Your Security Is “Appropriate”

5、How to Measure Ecosystem Impacts
6、IMF Case Study
7、Math Is Hard: Compliance to Continuous Risk Management
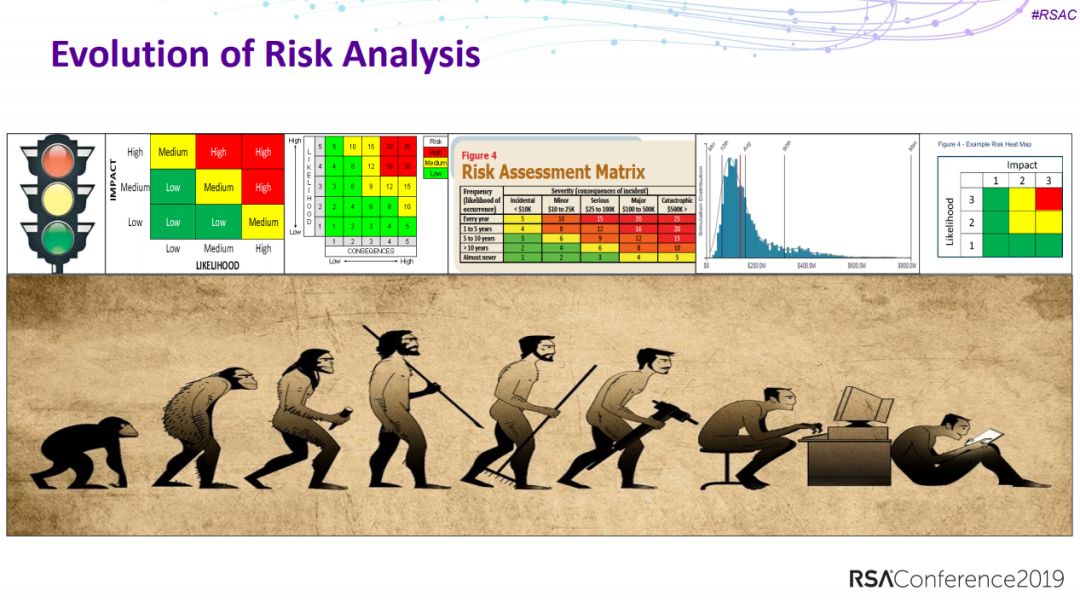
8、NIST Cybersecurity Framework and PCI DSS

9、直面数据安全
The Metrics Manifesto
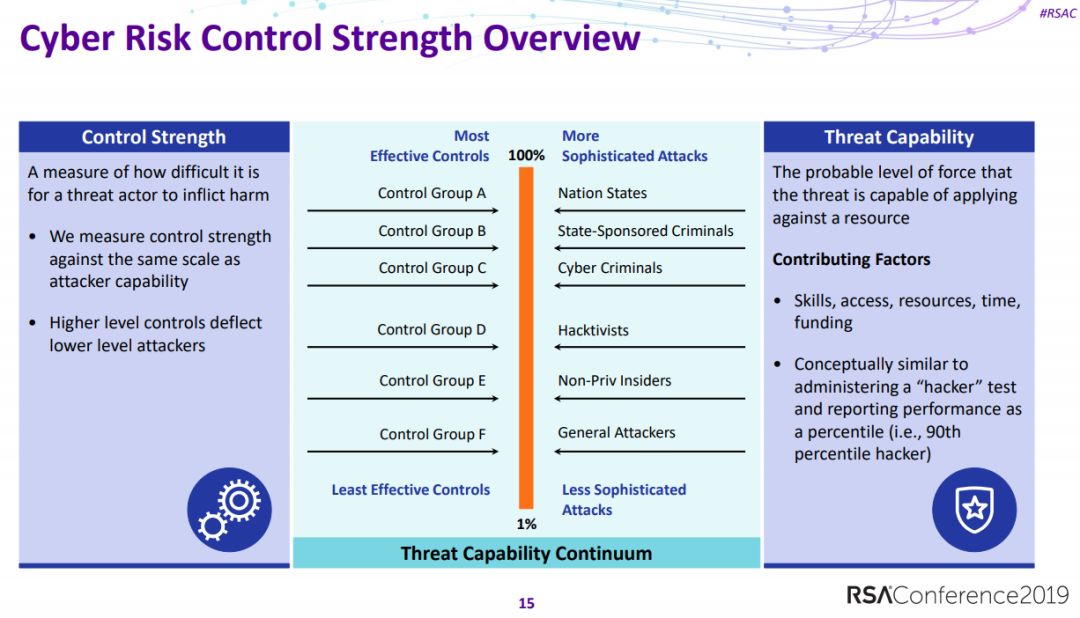
10、基于风险模型的虚拟渗透测试
Virtual Pen Testing Using Risk Models
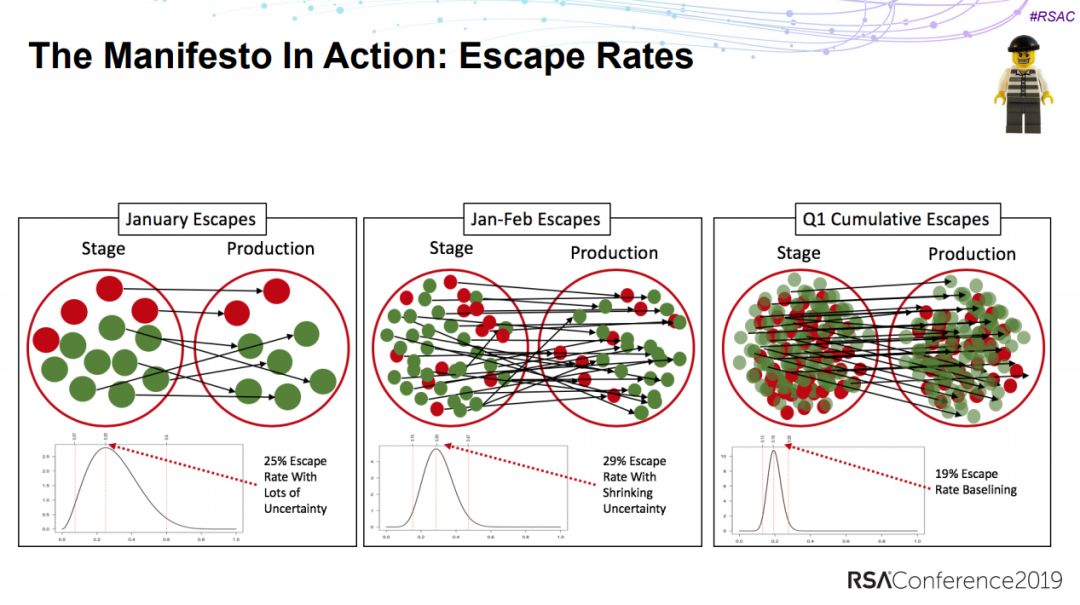
11、如何量化数据泄露造成的影响
We’re Not in Kansas Anymore: Measuring the Impact of a Data Breach

专题六丨安全中的人文元素Human Element
1、自动化 vs人肉
Automation vs. Human Eyes: Optimizing Human Intuition for Success

2、Awareness at Scale: Creating Risk-Aware Cultures in Big Companies
如何在大型公司内建立有风险意识的文化
3、如何在有限的预算下建立安全体系
Cheaper by the Dozen: Application Security on a Limited Budget

4、计算机战争与心理学管理
Cyber-Influence: Cyberwar and Psychological Operations

5、一个关于安全分散设置的故事
Democratizing Security: A Story of Security Decentralization

6、事件分析的艺术
Don’t Hand Me That! The Art of Incident Analysis

7、如何低成本控制用户行为
The Art of the Nudge, Cheap Ways to Steer User Behavior

8、网络文化黑客的盛行
The Rise of the Cyber-Culture Hacker

专题七丨身份认证Identity
1、黑掉多因素认证的12种方式
12 Ways to Hack MFA

2、4G到5G演进趋势下的深度安全预览
4G to 5G Evolution: In-Depth Security Perspective

3、如何欺骗生物识别认证?
Are Spoof-Proof Biometrics Really Possible?

4、Building Identity for an Open Perimeter
如何在开放的边界建立身份识别
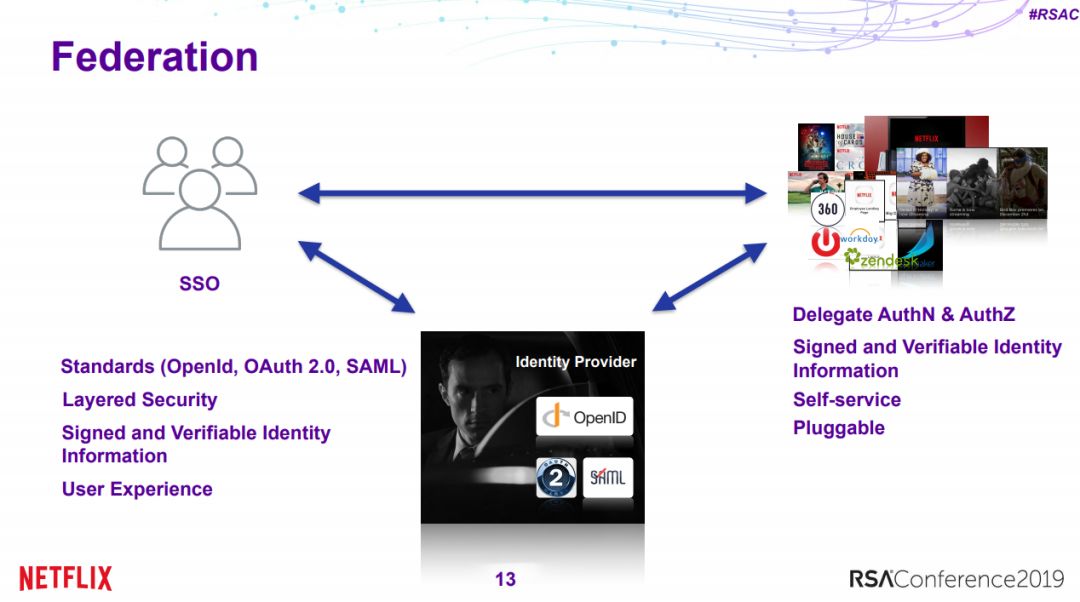
5、在旧组织中快速建立自动化的现代应用认证体系
Delivering Automated, Modern Enterprise App Auth in Old Orgs, Quickly
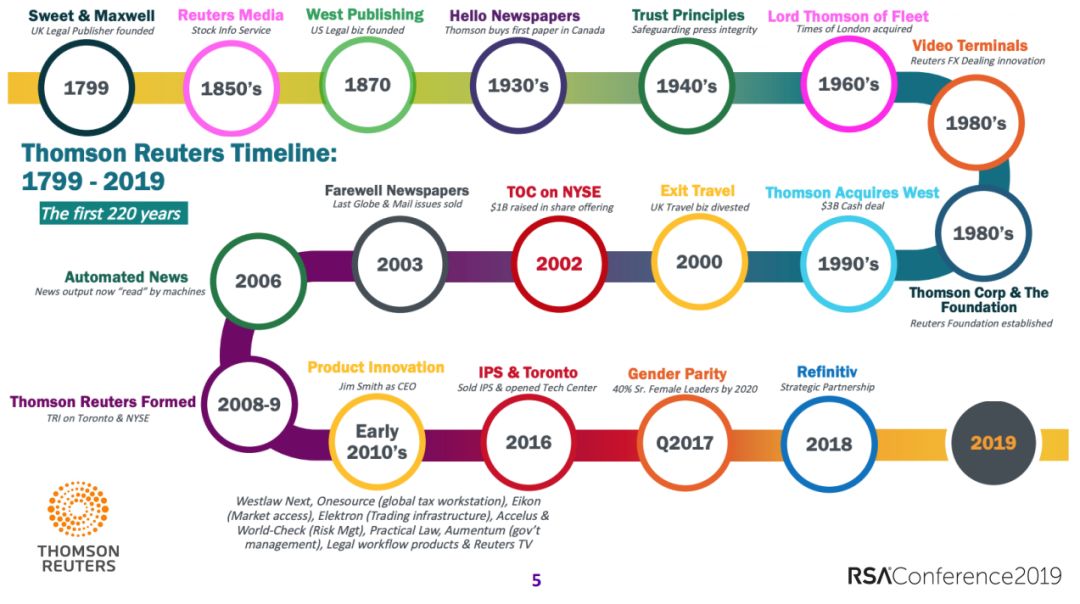
专题八丨安全法律遵从Law
1、加密货币黑客和区块链科技的法律环境
Cryptocurrency Hacking and the Legal Climate for Blockchain Technology

2、Cybersecurity: Federalism as Defense-in-Depth

3、DHS Hackers and the Lawyers Who Advise Them

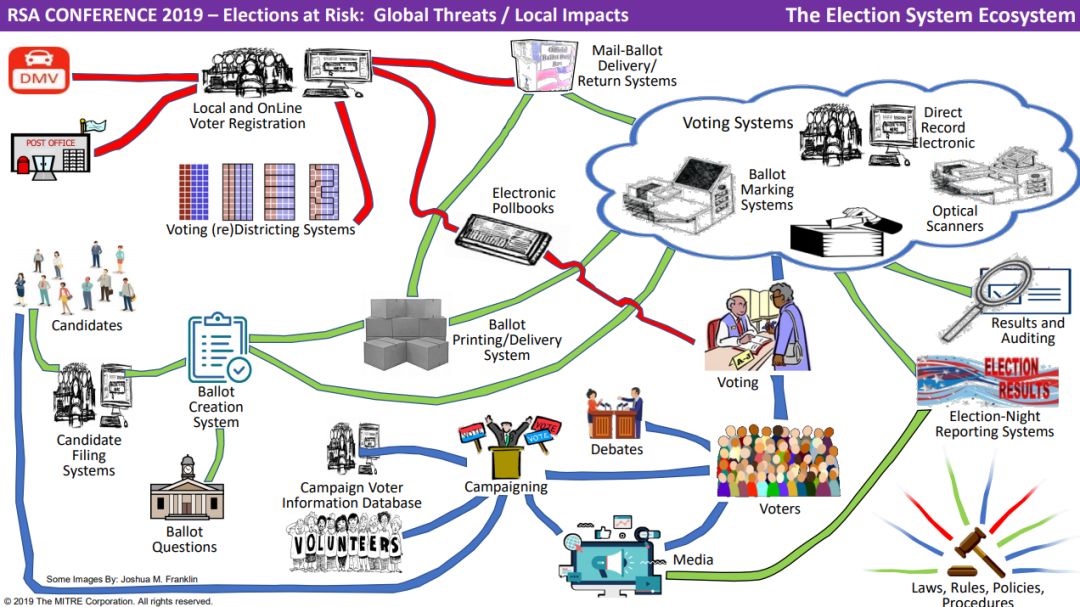
4、Elections at Risk: Global Threats / Local Impact
5、2019网络安全法规热点话题
Hot Topics in Cyber-Law 2019

专题九丨机器学习与人工智能
Machine Learning & Artificial Intelligence
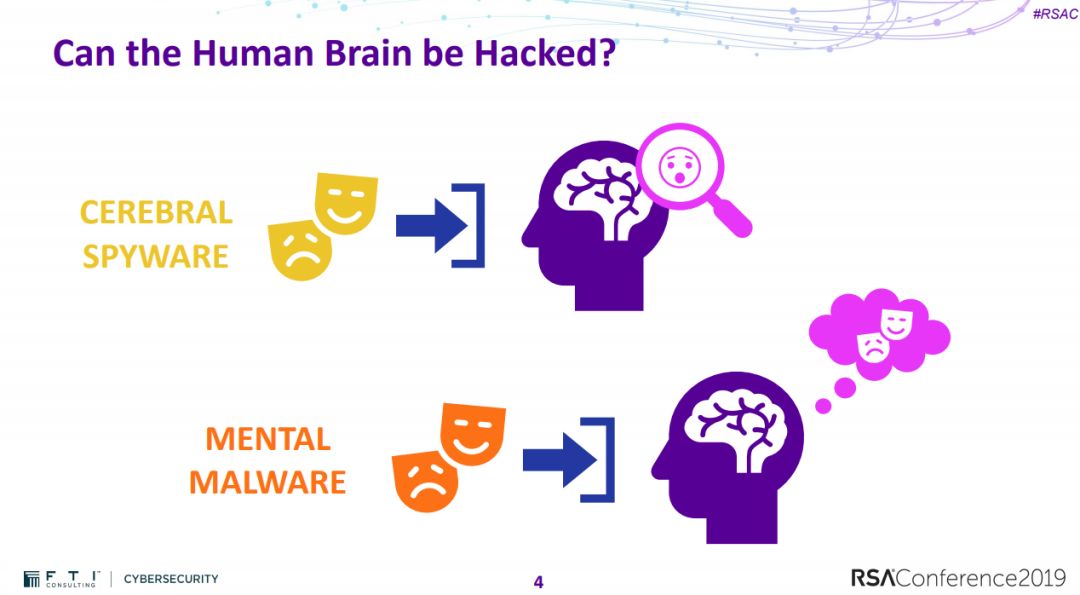
1、如何黑进人类的大脑?
AI: Hacking without Humans How Can Human Brains Be Hacked?
2、用于网络空间安全风险管理的机器学习工具箱
Machine Learning Toolbox for Cybersecurity Risk Management

专题十丨移动与IoT安全
Mobile & IoT Security
1、Achieving Operational Security Excellence in Connected IoT Solutions

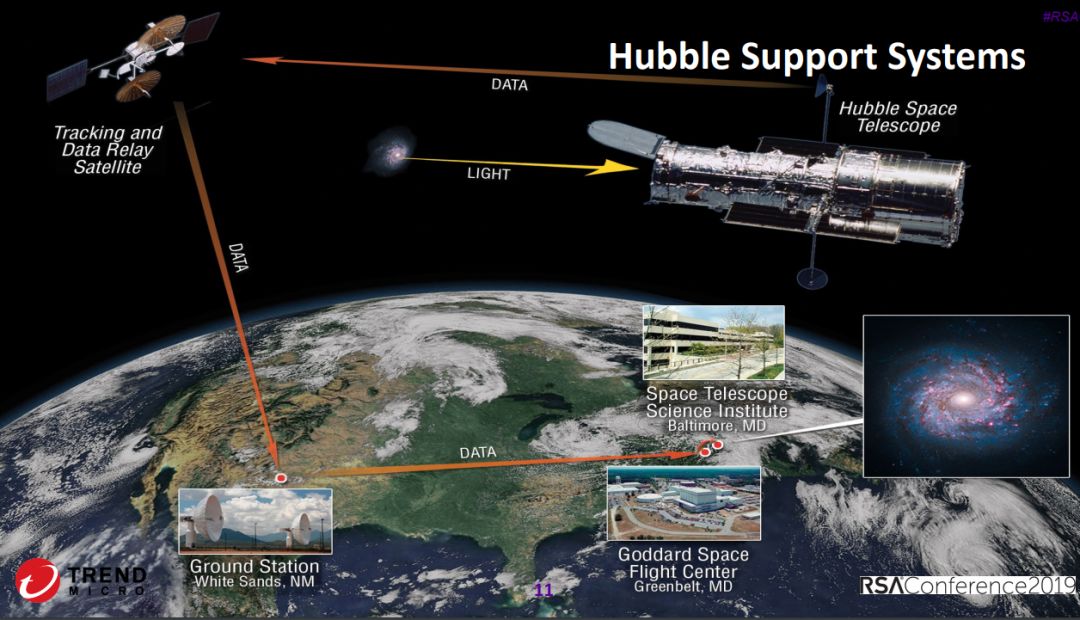
2、IoT与卫星安全需求
Attack Vectors in Orbit: The Need for IoT and Satellite Security
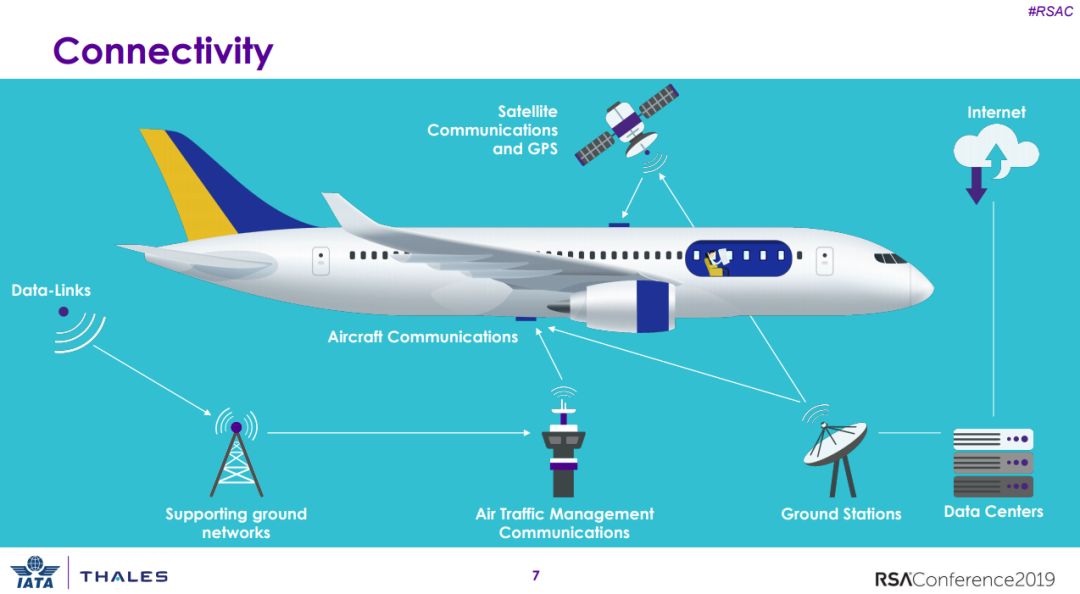
3、航空业网络安全:让翅膀永不停
Aviation Cybersecurity: Keeping the Wings On
4、人工智能蜂群机器人
Evolution of AI-Bot Swarming Intelligence with Robots

5、Japan’s New Cybersecurity Strategy to Close an IoT Gap
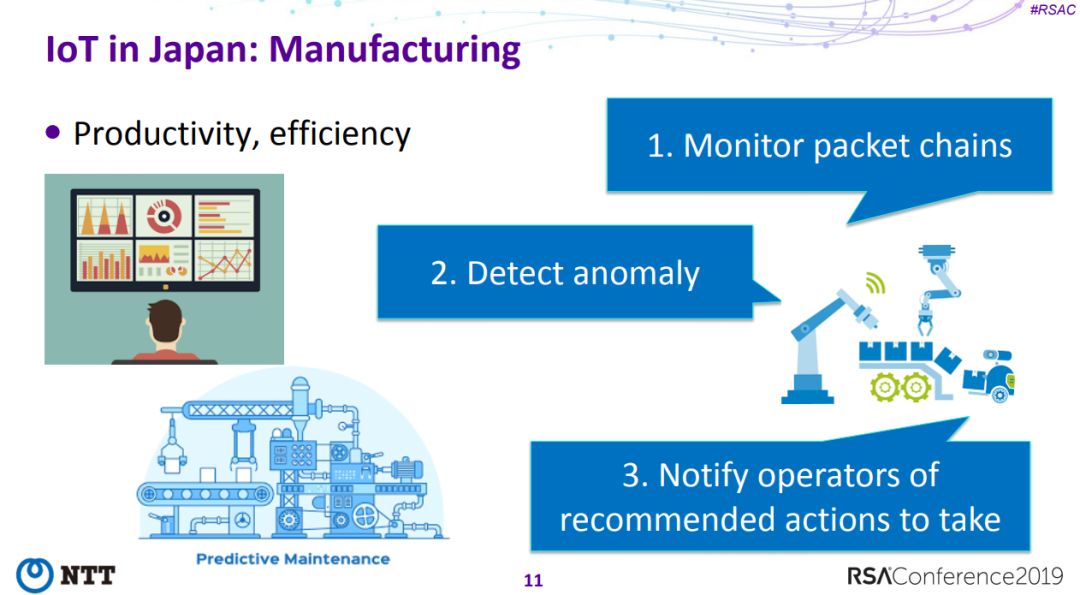
6、Why Industrial IoT Security Is Really about Saving Lives

话题还有很多,就不一一列举了。
下载地址:https://share.weiyun.com/50GZ5cP
声明:本文来自特大号,版权归作者所有。文章内容仅代表作者独立观点,不代表安全内参立场,转载目的在于传递更多信息。如有侵权,请联系 anquanneican@163.com。
